-
Background reading: Project management and project planning
- Activity 10.2 Background reading :chapter 22
- Activity 10.2 Background reading :chapter 23 and chapter 3.3 & 3.4
- 3.3 Agile project management
- 3.4 Scaling agile methods
-
Topics Covered
- 📹 Project Risk Management (Kheder, 2014) data source from Youtube, accessed date on 11/06/16)
- 📹 Managing People (WDA, 2013) data source from Youtube, accessed date on 07/06/16)
- 📹 Teamwork (TheArtmadillo, 2010) data source from Youtube, accessed date on 07/06/16)
IT Project Management
Concerned with activities involved in ensuring that software is delivered on time and on schedule and in accordance with the requirements of the organisations developing and procuring the software.
IT Project management is needed because software development is always subject to budget and schedule constraints that are set by the organisation developing the software.
📹 Why software project management is different? (date source: youTube, 2014) Accessed date:06/06/2016
Success Criteria
- Deliver the software to the customer at the agreed time.
- Keep overall costs within budget.
- Deliver software that meets the customer’s expectations.
- Maintain a coherent and well-functioning development team.
- 💡 Project success factors (Standish group, 2013) Accessed date: 07/05/2016
Software Management Distinctions
- The product is intangible.
Software cannot be seen or touched. Software project managers cannot see progress by simply looking at the artefact that is being constructed.
- Many software projects are 'one-off' projects.
Large software projects are usually different in some ways from previous projects. Even managers who have lots of previous experience may find it difficult to anticipate problems.
- Software processes are variable and organisation specific.
We still cannot reliably predict when a particular software process is likely to lead to development problems.
- 📹 Why Projects Fail? (Carr,2011) data source from Youtube, accessed date on 07/06/16)
Factors Influencing Project Management
- Company Size.
- Software Customers.
- Software Size.
- Software Type.
- Organisational Culture.
- Software Development Processes.
These factors mean that project managers in different organisations may work in quite different ways.
Universal Management Activities
- Project Planning
Project managers are responsible for planning. estimating and scheduling project development and assigning people to tasks. Covered in Chapter 23.
- Risk Management
Project managers assess the risks that may affect a project, monitor these risks and take action when problems arise.
- People Management
Project managers have to choose people for their team and establish ways of working that leads to effective team performance.
Management Activities
- Reporting
Project managers are usually responsible for reporting on the progress of a project to customers and to the managers of the company developing the software.
- Proposal Writing
The first stage in a software project may involve writing a proposal to win a contract to carry out an item of work. The proposal describes the objectives of the project and how it will be carried out.
XXXXX -
Risk Management
-
Risk Management
Risk Management is concerned with identifying risks and drawing up plans to minimise their effect on a project.
- Software risk management is important because of the inherent uncertainties in software development.
These uncertainties stem from loosely defined requirements, requirements changes due to changes in customer needs, difficulties in estimating the time and resources required for software development, and differences in individual skills.
- You have to anticipate risks, understand the impact of these risks on the project, the product and the business, and take steps to avoid these risks.
Video: 📹 Introduce Risk Management (data source: youTube: Quailtygurus,2013) (17:57 minutes long) Accessed date: 11/06/16.
Risk Classification
There are two dimensions of risk classification
- The type of risk (technical, organisational, ..)
- What is affected by the risk:
Project risks affect schedule or resources;
Project risks affect the quality or performance of the software being developed;
Business risks affect the organisation developing or procuring the software.
Video: 📹 Manage Risk in Projects (data Data source: youTube: David, 2013) Accessed date: 07/06/2016
Examples of Project, Product, and Business Risks
Risk Affects Description Staff Turnover Project Experienced staff will leave the project before it is finished. Management Change Project There will be a change of organizational management with different priorities. Hardware Unavailability Project Hardware that is essential for the project will not be delivered on schedule. Requirements Changes Project and Product There will be a larger number of changes to the requirements than anticipated. Specification Delays Project and Product Specifications of essential interfaces are not available on schedule. Size Underestimate Project and Product The size of the system has been underestimated. CASE Tool UnderPerformance Product CASE tools, which support the project, do not perform as anticipated. Technology Change Business The underlying technology on which the system is built is superseded by new technology. Product Competition Business A competitive product is marketed before the system is completed. XX -
The Risk Management Process
- 💡 Risk Identification
Identify project, product and business risks;
- 💡 Risk Analysis
Assess the likelihood and consequences of these risks;
- 💡 Risk Planning
Draw up plans to avoid or minimise the effects of the risk;
Video: 📹 The Project Management Plan - Part 1 (data source: youTube: Dave Litten, 2011) Accessed date: 07/06/2016.
Video: 📹 The Project Management Plan - Part 2 (data source: youTube: Dave Litten, 2011) Accessed date: 07/06/2016 .
- 💡 Risk Monitoring
Monitor the risks throughout the project;
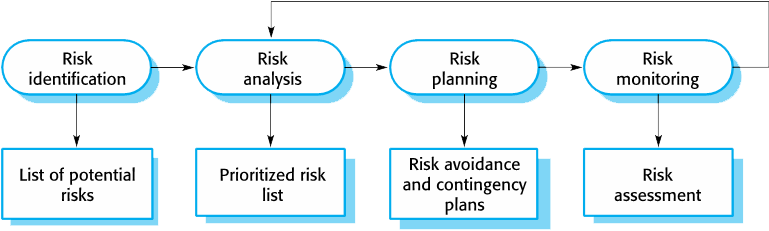
Risk Register
This collection of risks is called the risk register. A risk register is a document that contains results of various risk management processes, often displayed in a table or spreadsheet format.
💡 Examples of Different Risk Types
XXXRisk identification is the process of understanding what potential risk events might damage or gain a particular project. It is important to identify potential risks as soon as possible.
There are several tools and techniques for identifying risks, such as:
- Brainstorming
- Delphi Technique
- Interviewing
- SWOT (Strength, Weakness, Opportunities and Threats)
- Survey.
How to identify risks in IT projects? A checklist of common risks may be used to identify risks in a project:
- Technology Risks
- Organizational Risks
- People Risks
- Requirements Risks
- Estimation Risks.
XRisk Analysis
- Assess probability and seriousness of each risk.
- Probability may be very low, low, moderate, high or very high.
- Risk consequences might be catastrophic, serious, tolerable or insignificant.
XPlanning Risk ManagementIt is the process of deciding how to approach and plan for risk management activities for a project, and the main output of this process is a risk management plan. In addition to risk management plan, many IT projects also include contingency, fall-back and contingency reserves plans.
Consider each Risk and Develop a Strategy to Manage that Risk.
Avoidance strategies
- The probability that the risk will arise is reduced;
Minimisation strategies
- The impact of the risk on the project or product will be reduced;
Contingency plans
- If the risk arises, contingency plans are plans to deal with that risk.
XRisk Monitoring
- Assess each identified risks regularly to decide whether or not it is becoming less or more probable.
- Also assess whether the effects of the risk have changed.
- Each key risk should be discussed at management progress meetings.
XRisk Type Possible Risks Estimation The time required to develop the software is underestimated. (12)
The rate of defect repair is underestimated. (13)
The size of the software is underestimated. (14)Organisational The organisation is restructured so that different management are responsible for the project. (6)
Organisational financial problems force reductions in the project budget. (7)People It is impossible to recruit staff with the skills required. (3)
Key staff are ill and unavailable at critical times. (4)
Required training for staff is not available. (5)Requirements Changes to requirements that require major design rework are proposed. (10)
Customers fail to understand the impact of requirements changes. (11)Technology The database used in the system cannot process as many transactions per second as expected. (1)
Reusable software components contain defects that mean they cannot be reused as planned. (2)Tools The code generated by software code generation tools is inefficient. (8)
Software tools cannot work together in an integrated way. (9)XRisk Probability Effects Organisational financial problems force reductions in the project budget (7). Low Catastrophic It is impossible to recruit staff with the skills required for the project (3). High Catastrophic Key staff are ill at critical times in the project (4). Moderate Serious Faults in reusable software components have to be repaired before these components are reused. (2). Moderate Serious Changes to requirements that require major design rework are proposed (10). Moderate Serious The organisation is restructured so that different management are responsible for the project (6). High Serious The database used in the system cannot process as many transactions per second as expected (1). Moderate Serious The time required to develop the software is underestimated (12). High Serious Software tools cannot be integrated (9). High Tolerable Customers fail to understand the impact of requirements changes (11). Moderate Tolerable Required training for staff is not available (5). Moderate Tolerable The rate of defect repair is underestimated (13). Moderate Tolerable The size of the software is underestimated (14). High Tolerable Code generated by code generation tools is inefficient (8). Moderate Insignificant - 💡 Risk Identification
-
What If Questions
- What if several engineers are ill at the same time? People Risk
- What if an economic downturn leads to budget cuts of 20% for the project? Business Risk
- What if the performance of open-source software is inadequate and the only expert on that open source software leaves? Technology Risk
- What if the company that supplies and maintains software components goes out of business? Organisation Risk
- What if the customer fails to deliver the revised requirements as predicted? Requirement Risk
P.S. Try to identify what is the risk type for each question? Reveal Answers Hide Answers -
Strategies to Help Manage Risk
Risk Strategy Organisational financial problems Prepare a briefing document for senior management showing how the project is making a very important contribution to the goals of the business and presenting reasons why cuts to the project budget would not be cost-effective. Recruitment problems Alert customer to potential difficulties and the possibility of delays; investigate buying-in components. Staff illness Reorganise team so that there is more overlap of work and people therefore understand each other’s jobs. Defective components Replace potentially defective components with bought-in components of known reliability. Requirements changes Derive traceability information to assess requirements change impact; maximise information hiding in the design Organisational restructuring Prepare a briefing document for senior management showing how the project is making a very important contribution to the goals of the business. Database performance Investigate the possibility of buying a higher-performance database. Underestimated development time Investigate buying-in components; investigate use of a program generator. Risk Strategies
There are four basic strategies that can be used against negative risks:
- Risk Avoidance, or elimination of a specific risk, can be achieved by nullifying or removing the root cause of the risk. Not all risks can be wiped out, however some risks can be.
- Risk Acceptance, this would take the shape of acknowledging the risk but utilising a backup plan or a contingency plan.
- Risk Transference, would be the transfer of the risk on to a relevant third party.
- Risk Mitigation, is basically reducing the impact a risk can have on the project, or the likelihood of it occurrence.
-
Risk Indicators
Risk Type Potential Indicators Estimation Failure to meet agreed schedule; failure to clear reported defects. Organisational Organisational gossip; lack of action by senior management. People Poor staff morale; poor relationships amongst team members; high staff turnover. Requirements Many requirements change requests; customer complaints. Technology Late delivery of hardware or support software; many reported technology problems. Tools Reluctance by team members to use tools; complaints about CASE tools; demands for higher-powered workstations. -
Managing People
-
Managing People
- People are an organisation’s most important assets.
- The tasks of a manager are essentially people-oriented. Unless there is some understanding of people, management will be unsuccessful.
- Poor people management is an important contributor to project failure.
- 📹 Steve Jobs Talks About Managing People (data source: youTube: Ragni, 2010) Accessed date: 07/06/2016
X- Hiring the Right People (Sommerville,2014) Accessed date 5/06/2016
People Management Factors
- Consistency
Team members should all be treated in a comparable way without favourites or discrimination.
- Respect
Different team members have different skills and these differences should be respected.
- Inclusion
Involve all team members and make sure that people’s views are considered.
- Honesty
You should always be honest about what is going well and what is going badly in a project.
-
Motivating People
- An important role of a manager is to motivate the people working on a project.
- Motivation means organising the work and the working environment to encourage people to work effectively.
If people are not motivated, they will not be interested in the work they are doing. They will work slowly, be more likely to make mistakes and will not contribute to the broader goals of the team or the organisation.
- Motivation is a complex issue but it appears that their are different types of motivation based on:
- Basic needs (e.g. food, sleep, etc.);
- Personal needs (e.g. respect, self-esteem);
- Social needs (e.g. to be accepted as part of a group).
Human Needs Hierarchy
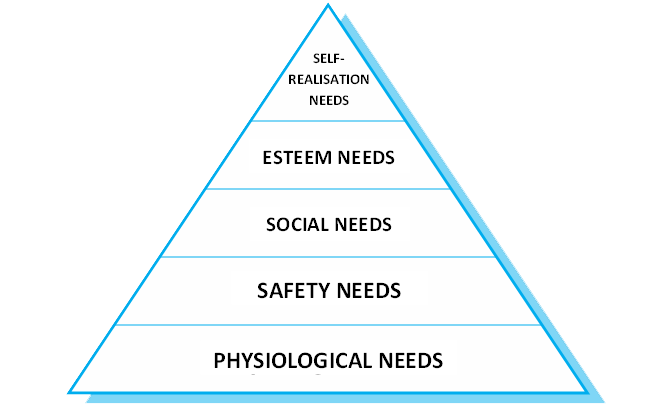
Need Satisfaction
- In software development groups, basic physiological and safety needs are not an issue.
- Social
Provide communal facilities;
Allow informal communications e.g. via social networking.
- Esteem
Recognition of achievements;
Appropriate rewards.
- Self-realisation
Training - people want to learn more;
Responsibility.
-
Case Study: Individual Motivation
Alice is a software project manager working in a company that develops alarm systems. This company wishes to enter the growing market of assistive technology to help elderly and disabled people live independently. Alice has been asked to lead a team of 6 developers than can develop new products based around the company’s alarm technology.
Alice’s assistive technology project starts well. Good working relationships develop within the team and creative new ideas are developed. The team decides to develop a peer-to-peer messaging system using digital televisions linked to the alarm network for communications. However, some months into the project, Alice notices that Dorothy, a hardware design expert, starts coming into work late, the quality of her work deteriorates and, increasingly, that she does not appear to be communicating with other members of the team. Alice talks about the problem informally with other team members to try to find out if Dorothy’s personal circumstances have changed, and if this might be affecting her work. They don’t know of anything, so Alice decides to talk with Dorothy to try to understand the problem.
After some initial denials that there is a problem, Dorothy admits that she has lost interest in the job. She expected that she would be able to develop and use her hardware interfacing skills. However, because of the product direction that has been chosen, she has little opportunity for this. Basically, she is working as a C programmer with other team members.
Although she admits that the work is challenging, she is concerned that she is not developing her interfacing skills. She is worried that finding a job that involves hardware interfacing will be difficult after this project. Because she does not want to upset the team by revealing that she is thinking about the next project, she has decided that it is best to minimize conversation with them.
Comments on Case Study
- If you don’t sort out the problem of unacceptable work, the other group members will become dissatisfied and feel that they are doing an unfair share of the work.
- Personal difficulties affect motivation because people can’t concentrate on their work. They need time and support to resolve these issues, although you have to make clear that they still have a responsibility to their employer.
- Alice gives Dorothy more design autonomy and organises training courses in software engineering that will give her more opportunities after her current project has finished.
-
Personality Types
- The needs hierarchy is almost certainly an over-simplification of motivation in practice.
- Motivation should also take into account different personality types:
- Task-oriented people, who are motivated by the work they do. In software engineering.
- Interaction-oriented people, who are motivated by the presence and actions of co-workers.
- Self-oriented people, who are principally motivated by personal success and recognition.
Motivation Balance
- Individual motivations are made up of elements of each class.
- The balance can change depending on personal circumstances and external events.
- However, people are not just motivated by personal factors but also by being part of a group and culture.
- People go to work because they are motivated by the people that they work with.
-
Teamwork
-
Teamwork
- Most software engineering is a group activity
The development schedule for most non-trivial software projects is such that they cannot be completed by one person working alone.
- A good group is cohesive and has a team spirit. The people involved are motivated by the success of the group as well as by their own personal goals.
- Group interaction is a key determinant of group performance.
- Flexibility in group composition is limited
Managers must do the best they can with the available people.
Video: 📹 Effective Team Work and Collaboration (data source: youTube: TheArtmadillo, 2010) Accessed date: 07/06/2016
XGroup Cohesiveness
- In a cohesive group, members consider the group to be more important than any individual in it.
- The advantages of a cohesive group are:
- Group quality standards can be developed by the group members.
- Team members learn from each other and get to know each other’s work; Inhibitions caused by ignorance are reduced.
- Knowledge is shared. Continuity can be maintained if a group member leaves.
- Refactoring and continual improvement is encouraged. Group members work collectively to deliver high quality results and fix problems, irrespective of the individuals who originally created the design or program.
-
Case Study: Team Spirit
Alice, an experienced project manager, understands the importance of creating a cohesive group. As they are developing a new product, she takes the opportunity of involving all group members in the product specification and design by getting them to discuss possible technology with elderly members of their families. She also encourages them to bring these family members to meet other members of the development group.
Alice also arranges monthly lunches for everyone in the group. These lunches are an opportunity for all team members to meet informally, talk around issues of concern, and get to know each other. At the lunch, Alice tells the group what she knows about organizational news, policies, strategies, and so forth. Each team member then briefly summarizes what they have been doing and the group discusses a general topic, such as new product ideas from elderly relatives.
Every few months, Alice organizes an ‘away day’ for the group where the team spends two days on ‘technology updating’. Each team member prepares an update on a relevant technology and presents it to the group. This is an off-site meeting in a good hotel and plenty of time is scheduled for discussion and social interaction.
-
The Effectiveness of a Team
- The People in the Group
You need a mix of people in a project group as software development involves diverse activities such as negotiating with clients, programming, testing and documentation.
- The Group Organisation
A group should be organized so that individuals can contribute to the best of their abilities and tasks can be completed as expected.
- Technical and Managerial Communications
Good communications between group members, and between the software engineering team and other project stakeholders, is essential.
Selecting Group Members
- A manager or team leader’s job is to create a cohesive group and organize their group so that they can work together effectively.
- This involves creating a group with the right balance of technical skills and personalities, and organizing that group so that the members work together effectively.
- The people capability maturity model (Sommerville,2014) Accessed date 5/06/2016
Assembling a Team
- May not be possible to appoint the ideal people to work on a project
- Project budget may not allow for the use of highly-paid staff;
- Staff with the appropriate experience may not be available;
- An organisation may wish to develop employee skills on a software project.
- Managers have to work within these constraints especially when there are shortages of trained staff.
-
Group Composition
- Group composed of members who share the same motivation can be problematic
- Task-oriented - everyone wants to do their own thing;
- Self-oriented - everyone wants to be the boss;
- Interaction-oriented - too much chatting, not enough work.
- An effective group has a balance of all types.
- This can be difficult to achieve software engineers are often task-oriented.
- Interaction-oriented people are very important as they can detect and defuse tensions that arise.
-
Case Study: Group Composition
In creating a group for assistive technology development, Alice is aware of the importance of selecting members with complementary personalities. When interviewing potential group members, she tried to assess whether they were task-oriented, self-oriented, or interaction-oriented. She felt that she was primarily a self-oriented type because she considered the project to be a way of getting noticed by senior management and possibly promoted. She therefore looked for one or perhaps two interaction-oriented personalities, with task-oriented individuals to complete the team. The final assessment that she arrived at was:
Alice—self-oriented
Brian—task-oriented
Bob—task-oriented
Carol—interaction-oriented
Dorothy—self-oriented
Ed—interaction-oriented
Fred—task-oriented
-
Group Organisation
The way that a group is organised affects the decisions that are made by that group, the ways that information is exchanged and the interactions between the development group and external project stakeholders. Key questions include:
- Should the project manager be the technical leader of the group?
- Who will be involved in making critical technical decisions, and how will these be made?
- How will interactions with external stakeholders and senior company management be handled?
- How can groups integrate people who are not co-located?
- How can knowledge be shared across the group?
- Small software engineering groups are usually organised informally without a rigid structure.
- For large projects, there may be a hierarchical structure where different groups are responsible for different sub-projects.
- Agile development is always based around an informal group on the principle that formal structure inhibits information exchange
Informal Groups
- The group acts as a whole and comes to a consensus on decisions affecting the system.
- The group leader serves as the external interface of the group but does not allocate specific work items.
- Rather, work is discussed by the group as a whole and tasks are allocated according to ability and experience.
- This approach is successful for groups where all members are experienced and competent.
-
Group Communications
- Good communications are essential for effective group working.
- Information must be exchanged on the status of work, design decisions and changes to previous decisions.
- Good communications also strengthens group cohesion as it promotes understanding.
- Group Size
- The larger the group, the harder it is for people to communicate with other group members.
- Group Structure
- Communication is better in informally structured groups than in hierarchically structured groups.
- Group Composition
- Communication is better when there are different personality types in a group and when groups are mixed rather than single sex.
- The Physical Work Environment
- Good workplace organisation can help encourage communications.
-
Key Points
- Good project management is essential if software engineering projects are to be developed on schedule and within budget.
- Software management is distinct from other engineering management. Software is intangible. Projects may be novel or innovative with no body of experience to guide their management. Software processes are not as mature as traditional engineering processes.
- Risk management involves identifying and assessing project risks to establish the probability that they will occur and the consequences for the project if that risk does arise. You should make plans to avoid, manage or deal with likely risks if or when they arise.
- People management involves choosing the right people to work on a project and organizing the team and its working environment.
- People are motivated by interaction with other people, the recognition of management and their peers, and by being given opportunities for personal development.
- Software development groups should be fairly small and cohesive. The key factors that influence the effectiveness of a group are the people in that group, the way that it is organised and the communication between group members.
- Communications within a group are influenced by factors such as the status of group members, the size of the group, the gender composition of the group, personalities and available communication channels.
-
Glossary
ABCDFGHILMOPRSW
A
activity chart
- A chart used by project managers to show the dependencies between tasks that have to be completed. The chart shows that tasks, the time expected to complete these taskes, and the task dependencies. The critical path is the longest path (in terms of the time requried to complete the tasks) through the activity chart. The critical path defies the minimum time required to complete the project.
- Data source: Sommerville I. 2011"Software Engineering" 9th Edition. Pearson Pp.733
Return to TopB
Brainstorming
- A technique by which a group attempts to generate ideas or find a solution for a specific problem by amassing ideas spontaneously and without judgement
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G2
Budge at completion (BAC)
- The original total budget for a project.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G3
Return to TopC
CMM
- The software Engineering Institue's Capability Maturity Model, which is used to been superseded by CMMI, but is still widely used.
- Data source: Sommerville I. 2011"Software Engineering" 9th Edition. Pearson Pp.736
CMMI
- An integrated approach to process capability maturity modelling based on the adoption of good software engineering practice and integrated quality management. It sorts discrete and continuous maturity modelling and integrates systems and software engineering process maturity models.
- Data source: Sommerville I. 2011"Software Engineering" 9th Edition. Pearson Pp.736
constructive cost modeling (COCOMO)
- A family of algorithmic cost estimation models, COCOMO was first proposed in the early-1980s and has been modified and updated since then to reflect new technology and changing software engineering practice.
- Data source: Sommerville I. 2011 "Software Engineering" 9th Edition. Pearson Pp.737.
contingency allowances
- Provisions held by the project sponsor or organisation to reduce the risk for cost or schedule overruns to an acceptable level; also called contingency reserves.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G3
contingency plans
- Predefined actions that the project team will take if an identified risk event occurs.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G3
contingency reserves
- Provisions held by the project sponsor or organisation to reduce the risk of cost or schedule overruns to an acceptable level; also called contingency allowances.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G3
contract
- A mutually binding agreement that obligates the seller to provide the specified products or services, and obligates the buyer to pay for them.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G3
control metric
- A software metric that allows managers to make planning decisions based on information about the software process or the software product that tis being developed. Most control metrics are process metrics.
- Data source: Sommerville I. 2011 "Software Engineering" 9th Edition. Pearson Pp.737.
critical system
- A computer system whose failure can result in significant economic, human or environmental losses.
- Data source: Sommerville I. 2011 "Software Engineering" 9th Edition. Pearson Pp.737.
Return to TopD
deliverable
- A product or service, such as a technical report, a training session, a piece of hardware, or a segment of software code, produced or provided as part of a project.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G5
Delphi technology
- An approach used to derive a consensus among a panel of experts to make predictions about future development
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G3
Dependability
- The dependability of a system is an aggregate property that takes into account the system's safety, reliability, availability, security and other attributes. The dependability of a system reflects the extent to which it can be trusted by its users.
- Data source: Sommerville I. 2016 "Software Engineering" 10th Edition. Pearson Pp.762.
Return to TopF
fall back plans
- Plans developed for risks that have a high impact on meeting project objectives, to be implemented if attempts to reduce the risks are not effective.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G5
Return to TopG
Gantt Chart
- A standard format for displaying project activities and their corresponding start and finish dates in a calendar format; sometimes referred to as bar chart.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G6
Return to TopH
Hazard
- A condition or state in a system that has the potential to cause or contribute to an accident.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.764
Return to TopI
ISO 9000/9001
- A set of standards for quality management processes that is defined by the international standards organisation (ISO). ISO 9001 is the ISO standard that is most applicable to software development. These may be used to certify the quality management processes in an organisation.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.764
Return to TopL
legacy system
- A socio-technical system that is useful or essential to an organisation but which has been developed using obsolete technology or methods. Because legacy systems often perform critical business functions, they have to be maintained.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.765
Return to TopM
maintenance
- The process of making changes to a system after it has been put into operation.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.765
Return to TopO
outsourcing
- When an organisation acquires goods and/or sources from an outside source.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G8
overrun
- The additional percentage or dollar amount by which actual costs exceed estimates.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G8
Return to TopP
project
- A temporary endeavour undertaken to create a unique product, service, or result.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G10
project feasibility
- The first two phases in a project (concept and development) that focus on planning.)
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G10
Return to TopR
rework
- action taken to bring rejected items into compliance with product requirements or specifications or other stakeholder expectations.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk
- An undesirable outcome that poses a threat to the achievement of some objective. A process risk threatens the schedule or cost of a process; a product risk is a risk that may mean that some of the system requirements may not be achieved. A safety risk is a measure of the probability that a hazard will lead to an accident.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.770
risk acceptance
- accepting the consequences should a risk occur.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk averse
- having a low tolerance for risk
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk avoidance
- eliminating a specific threat or risk, usually by eliminating its causes.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk factors
- Numbers that represent overall risk of specific events, given their probability of occurring and the consequence to the project if they do occur.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk management
- The process of identifying risks, assessing their severity, planning measures to put in place if the risks arise and monitoring the software and the software process for risks.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.770
risk management plan
- a plan that documents the procedures for managing risk throughout a project
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk mitigation
- reducing the impact of a risk event by reducing the probability of tis occurrence.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk register
- a document that contains results of various risk management processes often displayed in a table or spreadsheet format.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk tolerance
- the amount of satisfaction or pleasure received from a potential payoff; also called risk utility
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G12
risk transference
- Shifting the consequence of a risk and responsibility for its management to a third party
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G13
Return to TopS
security
- The ability of a system to protect itself against accidental or deliberate intrusion. Security includes confidentiality, integrity and availability.
- Data source: Sommerville I. 2012 "Software Engineering" 10th Edition. Pearson Pp.771.
- Data source: Sommerville I. 2012 "Software Engineering" 10th Edition. Pearson Pp.745.
SWOT analysis
- Analysing, Strengths, weaknesses, opportunities and Threats; used to aid in strategic planning.
- Data source: Schwalbe K,2010 "Information Technology Project Management" 6th Edition, Cengage Pp.G14
system
- A system is a purposed full collection of interrelated component, of different kinds, which work together to deliver a set of services to the system owner and users.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.772
system of system
- A system that is created by integrating two or more existing systems.
- Data source: Sommerville I. 2016"Software Engineering" 10th Edition. Pearson Pp.773
Return to TopW
wilderness weather system
- A system to collect data about the weather conditions in remote areas.
- Data source: Sommerville I. 2016 "Software Engineering" 10th Edition. Pearson Pp.775.
Return to Top