-
Introduction
Once the passive reconnaissance phase is over, a penetration tester can initiate the Scanning phase. This is the active attempt to connect to a system to elicit a response and determine the services running on it. Scanning is often also defined as Active Reconnaissance and typically enables the attacker to establish information about IP addresses, services running on a computer and operating systems.
The main objective of scanning is to probe ports, keeping track of open TCP/IP ports that would be receptive to hacking and establish applications vulnerable to hacking.
Scanning is a 3-step sequence process [1]:
1. Locating a live system in a network.
2. Scanning the system for open ports and running services.
3. Scanning the system for vulnerabilities.
Scanning can also be used to identify/detect the target operating system (fingerprinting)
- The three steps are defined as follows:
- Network Scanning – checks live IP addresses. This is a procedure for identifying active hosts on a network.
- Port Scanning - determines open ports and active services in each of the identified live hosts. A series of messages are sent to a computer to learn which network services and associated "well-known" port number are running.
- Vulnerability Scanning – The active services are scanned for vulnerabilities to determine the presence of known flaws.
This lecture focuses on the first two phases of Scanning: Network and Port Scanning. Vulnerability Scanning is introduced next week.
-
Network Scanning - Identifying Live Hosts
The scanning methodology begins by trying to detect/identify active hosts on the target network (respond to probes or connections). This is used to provide an accurate map of the network and to create a list of accessible systems on the target network.
Ping is a useful utility that can be used to identify active machines and to measure the speed at which packets are moved from one host to another. Ping can also be used for resolving host names.
Unfortunately, the usefulness of ping for scanning is limited, due to firewalls and other security devices blocking ICMP echo requests at the network perimeter. Most modern networks and devices block ICMP packets by default. Especially when large networks are scanned. When a large number of ICMP echo requests is detected, a firewall or IDS can easily recognise the ping sweep and block it immediately. Therefore, just because a ping sweep doesn't return active hosts on a network does not mean they aren't available. Alternative methods should be attempted.
TCP SYN PING
One alternative method for identifying live machines is the TCP SYN Ping. This is a scan that sends a TCP packet (generally empty) with the SYN flag set, addressed to a selected port. If the port is open the target should reply with a SYN, ACK, but if the port is closed target replies with a RST flag. Either way it is possible to assume that the target is alive. On the downside, this scan is well known and can be easily spotted by modern systems –and it is often blocked.
UDP Ping
This scan uses a UDP packet sent to a port that it is hoped to be closed. The reason for this is that if the port is closed then an ICMP port unreachable packet is returned, otherwise no response is given. For this to work a closed destination port is essential, therefore a port from high range is often used.
List scan
An alternative method is to simply scan a DNS server to identify which hosts are registered to it. By using a reverse-DNS resolution to perform this scan, it is possible to lists every host on the network without sending any packets to the target. This has the advantage of being stealthy. Additionally, the hostname of the target may hint the role of the device. The big disadvantage is that the scan isn't really an active scan. It doesn't show availability, meaning that the host registered to the DNS server (and returning from the scan) may not actually be alive at the time of the scan.
ARP Ping
What if you need to scan for a live host within a Local Area Network? The answer is ARP Ping. ARP is an essential protocol which must be enabled to allow communication between hosts in a LAN. Therefore, whenever an ARP request is sent for a specific host, if the host is active a reply must be delivered.
IPv6
Due to the much larger size of IPv6 subnets in comparison to IPv4, it will become less feasible for traditional network scanning methods to detect open services for subsequent attacks, assuming the attackers are off-site and services are not listed in the DNS.
If administrators number their IPv6 subnets in 'random', non-predictable ways, attackers, will need to make use of different approaches to determine IPv6 host addresses to target
-
Port Scanning - Identifying open ports and services
With knowledge of the network range and a list of active devices, the next step is to locate any open ports and access points, and identify the services running that might give an attacker a route in.
Port scanning is the method used to check for open ports. The process involves probing each port to determine which ports are open, by sending a data packet to a port to identify the state of the port and the services and applications running on the target.
- TCP ports can have three states:
- open – the target accepts incoming request on that port
- closed/unfiltered – not accepting connectivity
- filtered – some filter is applied that is preventing the port from being probed.
Many types of scanning techniques exist. The particular methodology depends on the objective of the attack and the target platform. Scans should often be intended to be stealthy. TCP scans exploit either the TCP handshake process or the TCP connection maintenance process. Every TCP connection must first be established with a three-way handshake between the client host and the server. A three-way handshake sets the initial parameters for connection and ensures that both hosts can communicate with each other.
NOTE - LEGAL ISSUES A PORT SCAN IS LIKE A RINGING A DOORBELL TO SEE WHETHER SOMEONE IS AT HOME. THE POLICE CAN'T DO ANYTHING ABOUT IT - HAVE TO WAIT UNTIL A CRIME IS COMMITTED. THE POLICE MIGHT GIVE IT MORE CONSIDERATION IF THE DOORBELL IS REPEATEDLY RUNG CAUSING THE HOMEOWNER TO COMPLAIN OF HARASSMENT. SOMETIMES, IF A COMPUTER SYSTEM IS AFFECTED TOO MUCH BY A PORT SCAN, ONE CAN ARGUE THAT THE PORT SCAN WAS, IN FACT, A DENIAL-OF-SERVICE (DOS) ATTACK, WHICH IS AN OFFENSE. PORT SCANNING IS NOT A CRIME, BUT YOU SHOULD STILL SEEK TO OBTAIN PERMISSION BEFORE SCANNING A NETWORK.TCP Connect Scan
TCP Connect Scan is where a full connection is opened to the target by a three-way TCP/IP handshake. It is the most basic and reliable but it is easily detected & blocked by firewalls.
The three-way handshake establishes connection from both ends and likewise can be terminated from both ends individually. If a port is listening, the connection will succeed, but if it is closed the server responds with a RST+ACK flag. This is the most reliable form of TCP scanning.
TCP SYN Scan
Often referred to as half open scan, the SYN Scan send connection requests to the target and waits for its response. If a port is open the target replies with a SYN, ACK otherwise with a RST flag set. If no response is received the port is probably filtered. Used to be used to evade detection, as a stealth scan. Not so much these days as it can be spotted by firewalls, IDSs and IPSs.
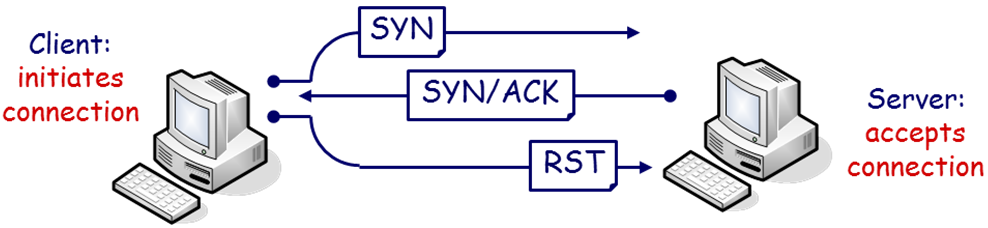
Figure 1 - TCP SYN Scan XMAS Scan
Sets the FIN, PSH, and URG flags, lighting the packet up like a Christmas tree. This scan exploits a subtle loophole in the TCP RFC to differentiate between open and closed ports. Basically if a port is closed, it responds to an Xmas tree scan with a RST, while an open port remains silent and normally marked as open|Filtered
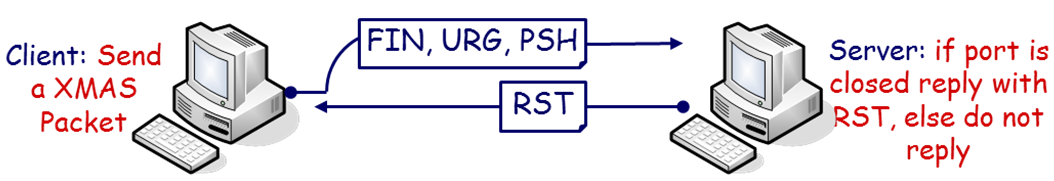
Figure 2 - XMAS Scan FIN Scan
These scan behave exactly the same as the XMAS Scan, except for the TCP flags set in the probe packets. A FIN is sent to the server. If a RST packet is received, the port is considered closed, while no response means it is open|filtered.
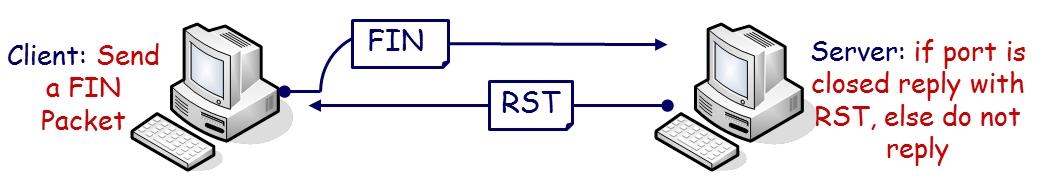
Figure 3 - FIN Scan Null Scan
Same as previously, this scan takes advantage of the same loophole in the TCP RFC. In this case however, the server is probed with no flags set. The server should return an RST packet when the port is closed, while no response is sent when open.
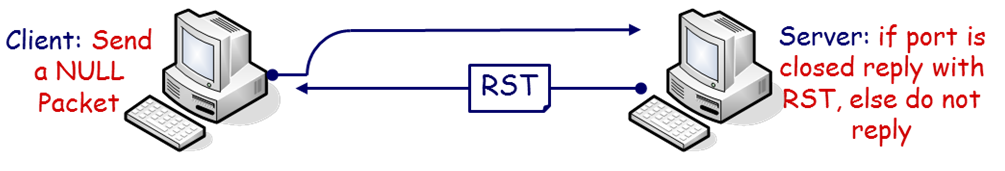
Figure 4 - NULL Scan UDP Scanning
As UDP is a much simpler protocol than TCP it is inherently unreliable. UDP represents the most evasive service ports because they respond in a different manner as a system is not required to respond to packets sent to an open UDP port. To find UDP ports, an attacker generally sends empty UDP datagrams. If the port is listening, the service should send back an error message or ignore the incoming datagram. If the port is closed, then most operating systems send back an "ICMP Port Unreachable" message. Thus, you can find out if a port is NOT open, and by exclusion determine which ports are open.
Advanced Techniques
One problem, from the perspective of an attacker attempting to scan a port, is that services listening on these ports log scans. They see an incoming connection, but no data, so an error is logged. Port scanners scan a host rapidly by firing off packets at different ports. Scanning very slowly (a day or more) becomes a stealth scan. There exist a number of stealth scan techniques (designed to go undetected by auditing tools) to avoid this. However, these are beyond the scope of this course and won’t be covered here.
-
Scanning Tools
Many scanning tools exist. Most of them are excellent and have unique features. So which one you chose is a matter of preference. Here only two very popular tools will be introduced: nmap and Hping.
Nmap
Nmap (Network mapper) [2] is an open source utility for network discovery and scanning, which uses raw IP packets to determine what hosts are available on a network. It is capable of discovering, amongst other things, what services those hosts are offering, what operating systems they are running, and what type of packet filters/firewalls are in use.
Nmap was designed to rapidly scan large networks, but works fine against single hosts. It runs on all major computer operating systems, and both console and graphical versions are available.
Nmap is an excellent network scanner with numerous options and features. One of its most efficient features is port scanning – i.e. the process of remotely scanning TCP and UDP ports to determine their state.
Hping
Hping [3] is a tool that allows the crafting of TCP/IP packets. One of its main features is the capability to forge packets from scratch using the command line interface. Any fields within the TCP/IP PDU can be modified. This could be used to simulate, for instance, spoofing attacks. In general, Hping is an excellent tool that can be used for security auditing and testing of networks.
-
Banner Grabbing
Banners are the welcome screens that divulge software version numbers and other host information to a network host. Banner information identifies the operating system, version number, and specific service packs, enabling vulnerabilities to establish. Once active nodes are discovered, the easiest method to discover important information about what type and version of services running on the open ports is by banner grabbing. Banner grabbing involves establishing a raw connection to an open port and documenting its response. Information sources: Telnet and FTP client, or Netcat.
-
Operating System Fingerprinting
Fingerprinting is a technique used to interpret the responses of a system in order to establish the operating system that is running on the target system. The advantage of fingerprinting over more robust scanning techniques is that it is less detectable. Fingerprinting exploits the fact that operating systems implement the TCP stack differently, meaning that specific systems respond in unique ways.
- The two different types of fingerprinting are:
- Passive fingerprinting - the act of identifying systems without injecting traffic or packets into the network.
- Active fingerprinting - sending malformed packets to the target in hope of eliciting a response that will identify it.
Passive fingerprinting
Passive banner grabbing refers to indirectly scanning a system to reveal its server's operating system its server’s operating system. Passive fingerprinting is based on the differential implantation of the stack and the various ways an operating system responds to it. Instead of relying on scanning the target host, it captures packets from the target host and studies it for signs that can reveal the operating system. It is less accurate than active fingerprinting but has the advantage of being stealthy.
Active fingerprinting
Active stack fingerprinting is also based on the fact that OS vendors implement the TCP stack differently. However, it actively sends packets to the target and check for their response. It is more powerful and accurate than passive OS fingerprinting, unfortunately it does not act in the same stealth manner.
-
Countermeasures
To minimise exposure to the dangers of port scanning using the principle of least privilege is an important concept. All unnecessary services should be disabled. Only needed ports should be kept open, the rest should be filtered or blocked. It is also possible to implement tool sets to detect and possibly thwart an attacker from acquiring information:
implementing firewalls that prevent internal systems from being scanned by blocking ping sweeps and port-scanning tools.
implementing intrusion detection systems (IDSs) and intrusion prevention systems (IPSs) in order to detect and alert an administrator to a ping sweep or scan taking place.
-
References
[1] – P. Engebretson, The Basics of Hacking and Penetration Testing: Ethical Hacking and Penetration Testing Made Easy, Syngress 2nd Ed., 2013.
[2] – Nmap Security Scanner, Gordon Lyon, aka Fyodor. Tool and manual available at:
🔗 https://nmap.org/[3] – Hping, created by Salvatore Sanfilippo. Tool and documentation available at:
🔗 http://www.hping.org/ -
Quiz
1. Can you name and explain the three distinct phases of the scanning process?
Answer:
1. The three distinct phases of the scanning process are:
1. Host discovery/Network Scanning – the process of determining whether a target system is live and capable of communicating with our machine;
2. Port scanning - the process of identifying the specific ports and services running a particular host;
3. Vulnerability Scanning - the process of locating and identifying weaknesses in the services and software running on a target machine.
2. Can you explain how the SYN scan is implemented?
Answer:
In a SYN scan, the scanning machine sends a SYN packet to the target and the target responds with a SYN/ACK (assuming the port is in use and not filtered) At this point, rather than sending the traditional ACK packet, the scanning machine sends an RST (reset) packet to the target. The reset packet tells the target machine to disregard any previous packets and close the connection between the two machines. If the port to which the SYN packet is sent is closed, the computer responds to the SYN packet with an RST/ACK packet.
3. Can you describe the process of a NULL port scan?
Answer:
Null scans are probes made with packets that violate traditional TCP communication. The null scan utilises packets that are devoid of any flags. An open port on the target system will send no response back, whereas a closed port will respond with an RST packet.