-
Introduction
Having established the target's operating system and applications, the next task is to research security vulnerabilities. Vulnerability scanning is the process of proactively identifying vulnerabilities of computer systems on a network. During the attack/exploitation phase, a hacker can exploit those weaknesses in order to gain access to the system. It is therefore essential that these are discovered in a timely manner.
Vulnerability scanning attempts to locate and identify weaknesses in the services and software running on a target machine. Many systems today can be exploited directly with little or no skill when a machine is discovered to have a known vulnerability.
Vulnerability scanning is often performed automatically. Scanners use a database of known vulnerabilities to check for weaknesses on a system.
Vulnerabilities associated with various network devices, servers, host operating systems and their associated network applications are often well documented, reported and patched by their vendors or by the information security community. It is important to mention that there is a difference in the severity of various vulnerabilities. Some vulnerabilities may present little opportunities for an attacker, whereas others will allow you to completely take over and control a machine with a single click of a button.
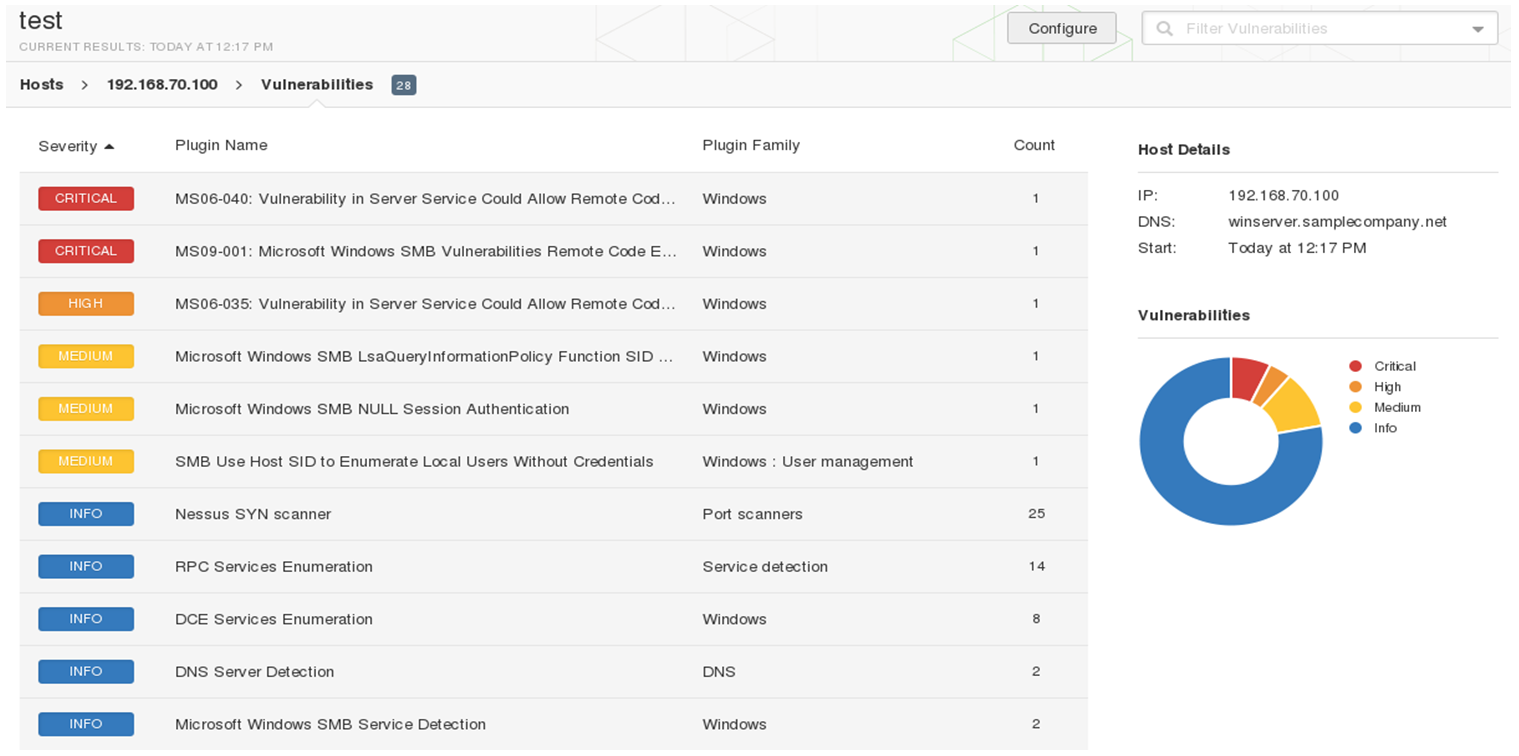
Figure 1 - Output from Nessus showing severity of found vulnerabilities -
Vulnerability Listings
Once discovered, vulnerabilities are published and listed. The most common examples of vulnerability listing systems is the Common Vulnerability & Exposure or CVE [1]
The CVE is a list of vulnerabilities containing an identification number, a description, and at least one public reference.
Major software providers also provide a listing of their product vulnerabilities and a corresponding patch that can be applied to fix the issue. The Microsoft Security Bulletin is an example of this [2].
-
Common Vulnerability Scoring System
- Vulnerability are rated according to their severity. The industry standard for assessing the severity of a vulnerability is the Common Vulnerability Scoring System or CVSS. This provides a method for scoring vulnerabilities based on a variety of measures:
- Access Vector Metric (AV) – How an attacker would exploit the vulnerability (Network, Adjacent, Local or Physical).
- Access Complexity Metric (AC)– How difficult is to exploit the vulnerability (Low or High).
- Privileges Required Metric (PR)– The level of access required to exploit the vulnerability (None, Low or High).
- User Interaction (UI) – Whether user interaction is required for the successful exploitation of the vulnerability (None or Required).
- Scope (S) - the ability for a vulnerability in one software component to impact resources beyond in others (Changed or Unchanged).
- Confidentiality Metric (C)– Type of information disclosure that could occur should an attacker successfully exploit the vulnerability (None, Low or High).
- Integrity Metric (I) – Type of information alteration that could occur should an attacker successfully exploit the vulnerability (None, Low or High).
- Availability Metric (A) – Type of disruption that could occur should an attacker successfully exploit the vulnerability (None, Low or High).
The CVSS score (often defined as vector) uses a single line format to report the ratings of a vulnerability. An example is given below:
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
The value for each metric is specific and it varies according to the metric itself. Their name is given above next to the metric itself. Once all values have been assigned, an equation is used to create a unique score also known as Base Score.
Refer to the Standard’s specification document [9] for a clear and more detailed explanation on metrics and score.
-
Common Vulnerabilities
A brief explanation of some of the most common types of vulnerabilities is given next.
Buffer Overflow
The way that applications run in a computer is by running their code in an allocated limited amount of memory. Buffer overflow occurs when a program is manipulated into placing more data into an area of memory that is allocated for that program. This allows an attacker to access certain areas of memory where malicious code could be run.
Buffer overflow vulnerabilities are responsible for many attacks with one of the most famous dating back to 1988 with the infamous Morris worm.
Arbitrary Code Execution
Arbitrary code execution allows attackers to run malicious software in the target system. If this is allowed through a remote connection the vulnerability can be very dangerous. An infamous example of this vulnerability is the MS08-067 vulnerability, which could allow remote code execution if an affected system received a specially crafted RPC request.
Injection Attacks
Injection attacks occur when a malicious user is able to send command via a web server to a backend system, bypassing security controls and fooling the backend system into believing that the request came from the web server itself. The most common example of this type of attacks is the SQL Injection attack. Generally, it works by allowing a user to send malicious SQL queries to a database running behind a web server. This is caused by improper input validation controls existing on the web site. For a good explanation and examples please refer to the OWASP SQL Test page [10]
Cross-Site Scripting.
Cross-Site scripting or XSS, is a common web vulnerability that allows a user to insert malicious code that is the executed by a visitor accessing the page. The aim is to trick a visitor into accessing a legitimate web site and executing malicious code placed there by a third party. Further reading is available from the OWASP web site [12].
Privilege Escalation
Privilege Escalation attacks attempt to increase the level of access than an attacker has when accessing a target system. This is a typical scenario of many attacks. Often attackers find themselves using a target machine with a user level access. Increasing that level of access becomes a priority as it would allow to run malicious software to the system.
A popular privilege escalation vulnerability was discovered in 2016 and it was named DirtyCOW. This was present in Linux for 9 years and allows for attackers to gain administrative rights easily.
Missing Patches
One of the main objectives of vulnerability scanning is to identify those devices in the network that have well-known vulnerabilities that can be fixed by software patches. Unfortunately, while this should be a routine task it is often neglected - often due to a lack of resources. The consequence is that organizations are often running unpatched servers and workstations and as such are easy target for attackers.
In addition to that many companies may still be running unsupported OSs such as Windows XP. As such they are at significant risk of attack.
Insecure Protocol Use
As you are aware by now, using older protocols in a network, present a major security flaw. The original protocols of the TCP/IP suite were designed without security in mind and as a consequence they allow for access to plain data traversing a network. Typical examples include HTTP, FTP and Telnet.
-
Zero-day vulnerabilities
A zero-day vulnerability refers to a flaw in software that is unknown to the creator/vendor/developer. If identified by a malicious hacker, this security hole can be exploited even before the vendor becomes aware of it. This exploit is generally named as a zero-day attack. Check the reference [8] for recent discovered zero day vulnerabilities.
-
Vulnerability Scanning Tools
While many vulnerability scanning products exist, both commercial and non-commercial, this section focuses on tools that we use either in the lab or we research. These are excellent tools, but they do not provide a complete picture of the products available in this area.
Nikto
Nikto [3] is a Web Vulnerability Scanner used to perform tests against web servers by searching for potentially dangerous files, outdated server versions and specific bugs and issues. It also checks for server configuration and options, and attempts to identify installed web servers and software.
Nessus
Nessus is a powerful and extensible security scanning tool developed by Tenable Network Security [4]. It provides a web based interface and operates by initially scanning a network for open ports and then determining from discovered ports what services and associated network application software is running on the target network.
Tenable Network Security produces several dozen new vulnerability tests each week (which they call plugins) and allow users of Nessus to update the functionality of the software to include these newly discovered vulnerabilities. These new vulnerability tests are available to the general public seven days after they are created, but they are available sooner to those willing to pay for Tenable Network Security’s commercial grade services.
Nexpose
Nexpose is a powerful Vulnerability Assessment tool distributed by Rapid7 [5]. Similarly to Nessus it uses a web based interface, where the user can configure and launch scans. The software starts by discovering the target system (network or host), then performing port scanning and evaluating any possible vulnerability against a database of known vulnerabilites.
OpenVAS
The Open Vulnerability Assessment System or OpenVAS [6] is a framework of several services and tools which include a vulnerability scanner. OpenVAS is open source and a popular alternative to the expensive commercial tools. This software is installed in the version of Kali Linux available in the labs.
-
OWASP
‘The OWASP Top Ten represents a broad consensus about most critical security risks to web applications. Project members include a variety of security experts from around the world who have shared their expertise to produce this list.’ [7]
The OWASP Top 10 for Web Apps has been recently updated. The figure below shows the current version (2017) compared to the previous one (2013):
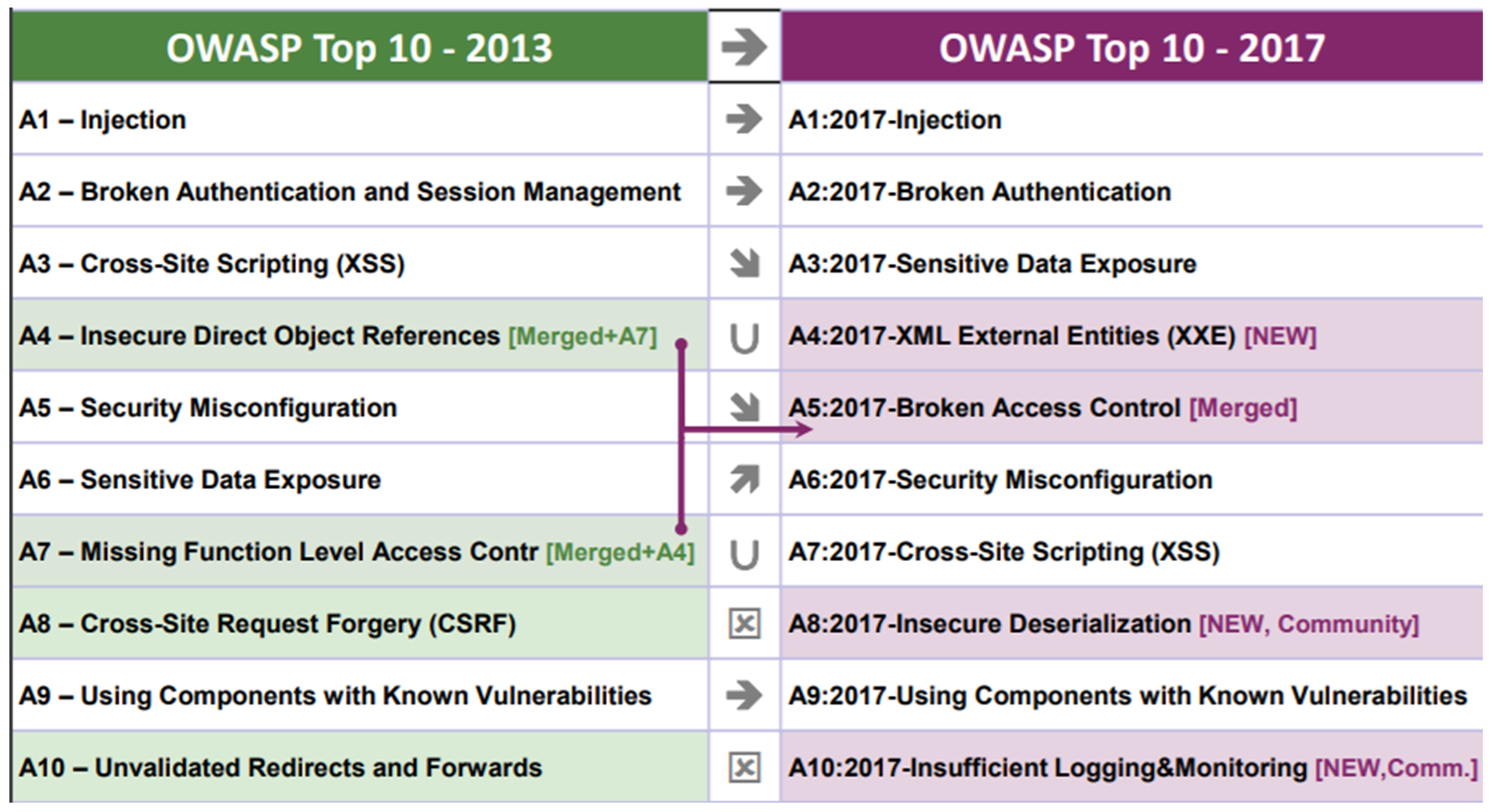
Figure 2 - OWASP 2017 -
References & Further Reading
[1] – CVE Common Vulnerability and Exposure. Available at: 🔗 https://cve.mitre.org
[2] – Microsoft Security Advisory and Bulleting. Available at: 🔗 https://technet.microsoft.com/en-us/security/bulletin/dn602597.aspx
[3] – Nikto Web Scanner. Available at: 🔗 https://github.com/sullo/nikto
[4] – Tenable, Nessus. Available at: 🔗 https://www.tenable.com/products/nessus-vulnerability-scanner
[5] - Nexpose, Vulnerability Scanner, Rapid7. Available at: 🔗 https://www.rapid7.com/products/nexpose/
[6] – OpenVAS Project. Available at: 🔗 http://www.openvas.org/
[7] – Owasp top 10. Available at: 🔗 https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
[8] – Recent Zero day exploit and vulnerabilities. Available at: 🔗 https://www.fireeye.com/current-threats/recent-zero-day-attacks.html
[9] - Common Vulnerability Scoring System v3.0: Specification Document: 🔗 https://www.first.org/cvss/specification-document
[10] - Testing for SQL Injection, OWASP. Available at: 🔗 https://www.owasp.org/index.php/Testing_for_SQL_Injection_(OTG-INPVAL-005)
[11] - SQL injection cheat sheet & tutorial: vulnerabilities & how to prevent SQL injection attacks, Veracode. Available: 🔗 https://www.veracode.com/security/sql-injection
[12] - Cross-site Scripting (XSS), OWASP. Available at: 🔗 https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
-
Quiz
1. Briefly explain the concept of a vulnerability assessment.
Answer:
Vulnerability Assessment is the process of locating and identifying known weaknesses in the services and software running on a target machine.
2. What is a zero-day vulnerability?
Answer:
A Zero-day vulnerability is one which code to exploit it appears on the first day that the vulnerability is announced. So no solution for it has been announced.
3. What is the main objective of a Privilege escalation attack?
Answer:
Privilege Escalation attacks attempt to increase the level of access than an attacker has when accessing a target system.