-
Exploitation
Exploitation is the phase that is most commonly associated with hacking. According to the Penetration Testing Execution Standard (PTES) [4], the exploitation phase ‘focuses solely on establishing access to a system or resource by bypassing security restrictions’. The main focus is to identify the main entry point into the organization and to identify high value target assets. It should be planned extensively by thoroughly completing the previous phases. The attack vector should be swift and concentrate on the target providing highest chances of success. Ultimately, exploitation is the process of launching an exploit against a vulnerable target. At times, it could be used to cause a Denial of Service.
As already mentioned, a vulnerability is a security flaw or weakness in an application or system that enables an attacker to compromise the target system. A compromised system can result in privilege escalation, denial-of-service, unauthorized data access, stolen passwords, and buffer overflows. An exploit is a realization of a vulnerability.
Generally an exploit is a program that takes advantage of a specific vulnerability and provides an attacker with access to the target system.
Exploits can be fleeting; meaning that they provide access only as long as the program that was exploited remains running. When the target machine reboots or the exploited process is stopped the shell is stopped. Attackers usually try to install backdoors for future access.
An exploit typically carries a payload and delivers it to the target system. Payloads are additional software or functionality installed and executed on the target system upon successful execution of an exploit.
-
Exploitation Frameworks
BeEF
The Browser Exploitation Framework or BeEF [1] is a powerful security tool used by professionals to test browsers for vulnerabilities. BeEF specifically focuses on the so called client side attack vectors, where a user visits a web page which contains exploits that allows access to a system via a browser vulnerability.
BeEF can also integrate Metasploit modules.
Metasploit
Metasploit [2] is an open source framework created by HD Moore in 2003. It was presented at Defcon 12 in 2004 as an exploit framework and development platform. Originally written in Perl, Metasploit was later re-written using the Ruby programming language. In October 2009 it was acquired by Rapid 7, but kept open source under the BSD License.
This tool changed the way ethical hackers developed and used their exploits. It also made it very easy to perform attacks against a computer system.
Metasploit is a tool which is used to achieve a certain attack vector. Whether it is attempting to crash a system, or take control of it, Metasploit offers the tool to best test a remote device. People confuse Metasploit as a tool which is used by (unethical) hackers; but it is really a framework for security professionals and researchers.
The Metasploit framework (MSF) is available for both Windows and Linux.
MSF is modular penetration testing platform that enables the writing, testing and the execution of exploit code. It contains a suite of tools that can be used to test security vulnerabilities, enumerate networks, execute attacks, and evade detection.
At its core, the Metasploit Framework is an open source collection of tools that provide a complete environment for penetration testing and exploit development. It’s a modular system based on a few core components: libraries, interfaces, modules and plugins [3].
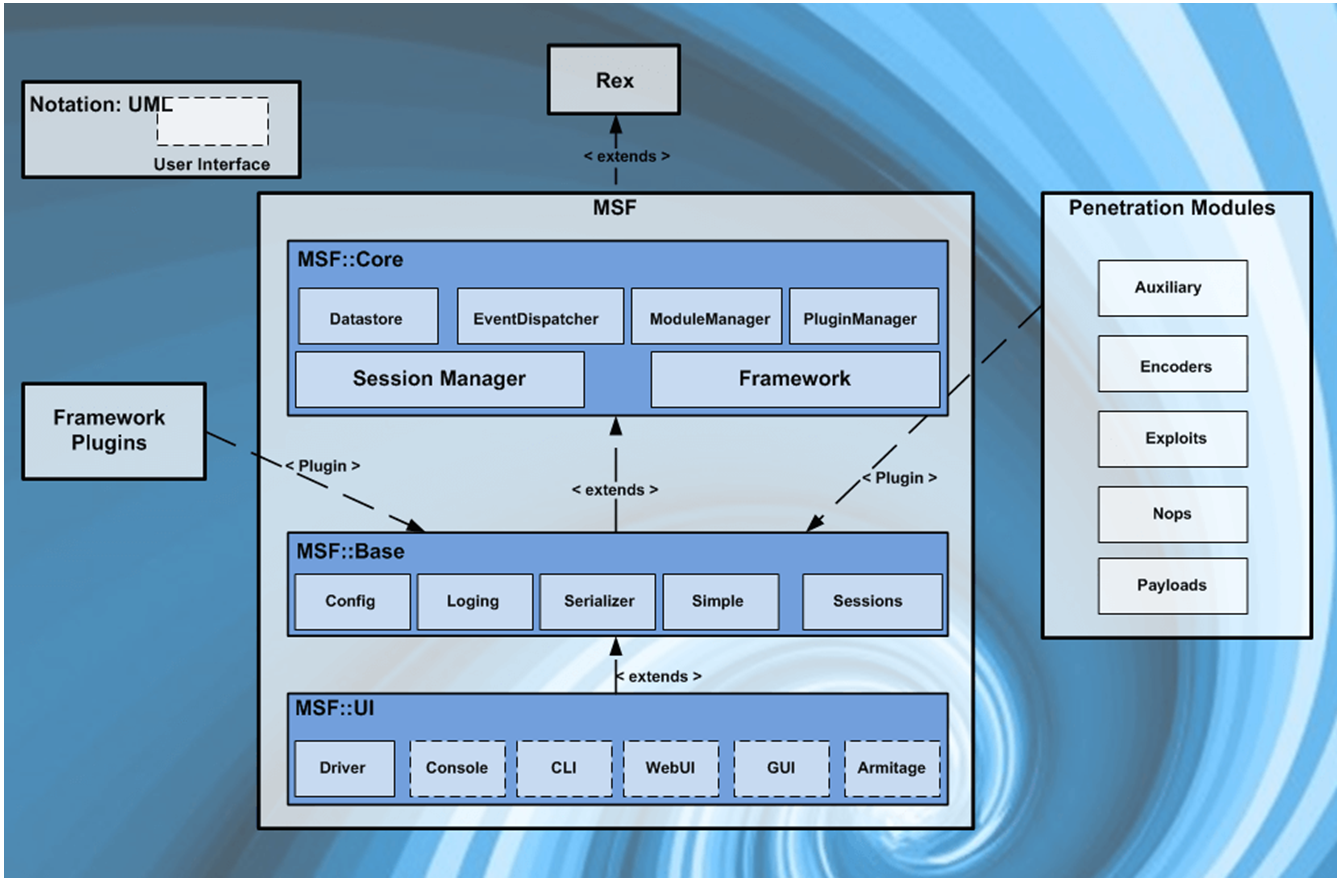
Figure 16 - MSF architecture – Picture downloaded from [3] -
Metasploit Interfaces
- Several interfaces exist for Metasploit [3]:
- Msfconsole – It provides a flexible way to use most features of the MSF. The msfconsole is the most popular interface to execute exploitations. Amongst its feature it allows execution of external commands (i.e. Linux shell commands) and allows for tab completion.
- MsfCLI: This is a Command-Line Interface. It is great for scripting but it is not supported as msfconsole. It only handles one shell at a time, making it impractical for client-side attacks. As of June 2015 MsfCLI has been removed from the framework. Using the option -x with msfconsole can obtain similar functionality.
- GUI: In the early days of Metasploit, a java based (msfGUI) and a web based (msfWeb) were available. These have been deprecated and substituted with a web interface for the Metasploit Community Edition and their commercial versions. This interface has been developed to facilitate network discovery and vulnerability verification for specific exploits.
- Armitage GUI – This is an excellent Java based GUI developed by Raphael Mudge. It visually streamlines the features within the MSF, such as host discovery, server-side and client-side exploitation, pivoting, and privilege escalation. Metasploit Armitage is automatically included with the MSF installation, even though it was developed as a separate project.
-
Modules
- Modules are the one of the core components of the MSF. A module is a piece of software that can perform a specific action. Examples include: exploitation, fuzzing, and scanning. Any task that can be performed with the MSF is defined within a module. Modules include:
- Exploits - An exploit module executes a sequence of commands to target a specific vulnerability found in a system or application. It takes advantage of a vulnerability to provide the attacker with access to the target system.
- Payloads - A payload is code that runs remotely often as an exploit successfully compromises a system. The payload enables users to define how they want to connect to a shell and what they want to do to the target system after taking control of it. Further explanation is given in [3], please make sure you check it.
- Auxiliary - it does not execute a payload and perform arbitrary actions. Examples of auxiliary modules include scanners, fuzzers, and denial of service attacks.
- NOPs - A NOP generator produces a series of random bytes that you can use to bypass standard IDS and IPS NOP sled signatures. Use NOP generators to pad buffers and keep the payload size consistent.
- Encoders - A payload encoder enables you to evade IDS and IPS signatures that are looking for specific bytes of a payload.
- Post Exploitations - enables you to gather more information or to gain further access to an exploited target system. Examples of post-exploitation modules include hash dumps and application and service enumerators.
Plugins
A plugin is a component that extends, enhances, or alters the functionality of the Metasploit Framework.
For instance, a plugin can be created to add a new feature or interface commands.
Mixins
A mixin allows the sharing of code between modules. This helps reduce the amount of duplicate code that exists between modules.
-
Meterpreter
Short for Meta-Interpreter, Meterpreter is an advanced payload that requires its own section. Meterpreter allows the writing of DLL files to dynamically create new features as you need them. Meterpreter is executed entirely from RAM memory, which helps avoiding standard Anti-Virus detection. It provides encryption using a custom XOR cypher. Not very secure, but capable of doing a good job at obfuscating the communication, thus allowing it to evade some IDS signatures.
Its main purpose is to provide complex and advanced features that could otherwise be implemented purely in assembly. DLL files can be uploaded and injected into a running process on a target computer after exploitation has occurred.
Capable of avoiding the creation of a new process as it executes in the context of the process being exploited.
Meterpreter provides a powerful command shell to the attacker. Once installed on the victim machine it allows attackers to execute commands as if they were sitting at the local machine. It provides a default set of commands. Examples include:
Fs – It allows for uploading and downloading files to and from the remote machine.
Getuid – it displays the user that the Meterpreter server is running as on the host.
Hashdump - it dumps the contents of the SAM database on the screen.
Shell – it presents the user with a standard shell on the target system.
NOTE:
Make sure that you study the Metasploit Unleashed tutorial available at [3] 🔗 https://www.offensive-security.com/metasploit-unleashed/
This is an excellent tutorial that provides a great guide for understanding and using Metasploit. You should be reading it in preparation for your exam and coursework. -
References & Further Reading
[1] – The Browser Exploitation Framework Project, BeEF. Available at: 🔗 http://beefproject.com/
[2] – Metasploit, Rapid7. Available at: 🔗 http://www.metasploit.com/
[3] – Offensive Security, Metasploit Unleashed, Free Online Security Training. Available at: 🔗 https://www.offensive-security.com/metasploit-unleashed/
[4] – The Penetration Testing Execution Standard. Available at: 🔗 www.pentest-standard.org/
-
Quiz
1. List the interfaces available for the Metasploit Framework.
2. What is the difference between an exploit and a payload?
Answer:
An exploit module executes a sequence of commands to target a specific vulnerability found in a system or application. It normally provides the attacker with access to the target system.
A payload is code that runs remotely often as an exploit successfully compromises a system. The payload enables users to define how they want to connect to a shell and what they want to do to the target system after taking control of it.
3. List the core components of the Metasploit Framework.