-
Introduction
The aim of this chapter is to introduce several types of attack vectors or methodologies that may be used by malicious hackers against a network infrastructure. The list can be long. Attacks come in many forms including malware, social engineering, insider threats, remote and many more.
In this chapter, focus is given exclusively to network attacks. These are attacks that can take advantage of some vulnerabilities within a network protocol or application, which can be exploited remotely via the network.
Network Attacks
In the last section, we discussed system vulnerabilities; we have used vulnerability scanners to identify possible vulnerabilities in operating systems. In this section we focus on the types of attack that can be launched against networks. These are not just of the hacker-for-gain type but also include vandalism against the network, much of which can be carried out by an attacker with low technical knowledge, perhaps using scripts downloaded from the internet.
We broadly classify network attacks into three categories: Reconnaissance, Access and Denial Of Service.
Reconnaissance attacks
Often defined as information gathering, reconnaissance is an unauthorised search and mapping of a target system. Reconnaissance could be divided into passive and active. Passive normally uses publicly available information obtained from social networks and the Internet in general. Not much can be done against this, other than making sure that staff are not posting online any information that may compromise the company’s security
Active reconnaissance involves actively scanning network infrastructure with the objective of identifying possible vulnerabilities. Counteracting active reconnaissance can be difficult. An effort should be made to ensure that secure protocols and encryption is used to guarantee confidentiality of communication.
Access attacks
Access attacks could involve remote attacks against vulnerable systems and/or attacks against weak passwords used in user authentication. We have already discussed some examples of password attacks in a previous section and during the lab exercises.
Defending against these types of attacks is difficult as a motivated attacker would try many possible methods to gain access, including social engineering and malware. Training and education is paramount, to at least mitigate some of the most common attack vectors.
From a technical point of view, a system administrator should ensure that the systems in use are fully patched and the use of complex passwords with regular changes is enforced.
Denial of Service Attacks
Denial of Service (DoS) attacks occur when an attacker disrupts the operation of a network rendering a service unusable to legitimate users. Many examples exist, some of which will be discussed later.
Nowadays these types of attacks come mostly in the form of a Distributed DoS. This is a large network of machines, compromised by malware, that sends a large amount of traffic against a target.
Again, similarly to the access attacks, if an attacker is well motivated and capable, the chances of stopping these attacks are limited. Only mitigation techniques can be put in place to limit the damage and the scope of the attack. These are device hardening, antivirus software, firewalls, etc.
-
Attacks examples
As we have seen previously attacks can come in many forms. This section aims at introducing some attacks that can take advantage of some weaknesses of the protocols studied above. Particularly, we will look at some Denial of service attacks that take advantage of the TCP and the IP protocols.
Denial of Service Attacks
TCP SYN flooding
SYN flooding exploits a flaw in three-way handshaking mechanism of the TCP/IP protocol to waste server resources and prevent legitimate connections from occurring. With a SYN flooding attack, the attacker sends multiple fake TCP SYN requests to establish a new connection with the target. Every request uses a spoofed random (unreachable) source IP addresses.
The host allocates resources to each request for connection and replies with an ACK/SYN to the nonexistent address. The target’s connection table fills up waiting for a final acknowledgement (ACK), which will never arrive. At some point the connection table fills up and all new connections (even legitimate ones) are ignored.
To clarify the process, review the normal TCP/IP three-way handshake mechanism from the figure below.
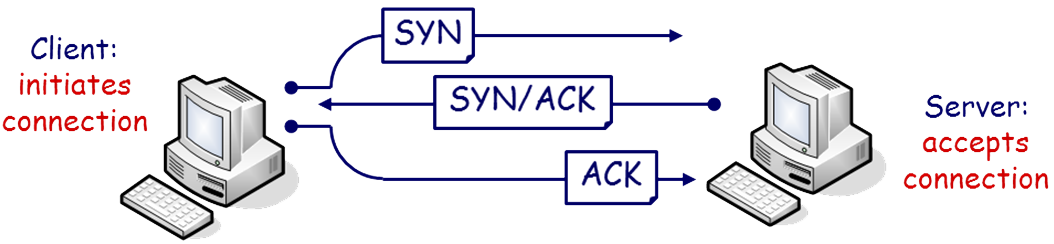
Figure 6 - Three-Way Handshake During a SYN Flood attack the malicious device does not complete the three-way handshake initiated by the originator. Because of a spoofed source address the target attempts to send the reply (SYN/ACK) to an unknown address as shown in Figure 7.
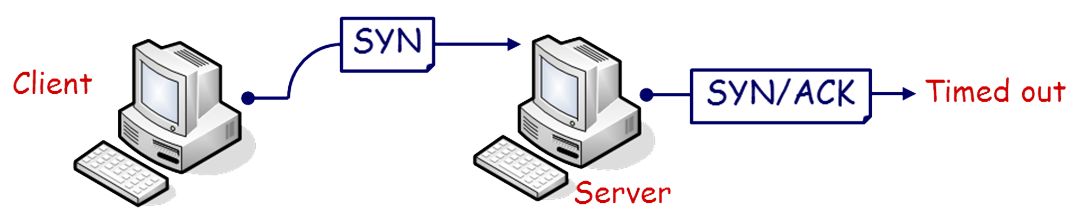
Figure 7 - TCP SYN Flooding Ping of Death Attack
Ping of death attacks are caused by an attacker deliberately sending an oversized IP packet (i.e. IP packet larger than the 65,536 bytes) using ICMP Pings.
Oversized packets are not allowed, but IP can be fooled into creating one using fragmentation. This allows a single IP packet, larger than the allowed MTU, to be broken down into smaller segments. When reaching destination the packet is reassembled by the Internet Protocol. If the reconstituted fragments add up to more than the allowed 65,536 bytes, the receiving operating system is unable to handle it and crashes.
This is an old attack. Modern operating systems have been patched to ensure they can handle it. However, many network administrator block ICMP in their networks to avoid future variations of this attack (as well as other types of attacks).
Smurf Attack
Packet flood DoS attacks send a deluge of traffic to a system, overwhelming its capability to respond to legitimate users. An example of this type of attack is the Smurf attack.
A Smurf attack exploits the ICMP echo request by sending a large amount of spoofed ping packets addressed to the broadcast address of a network with the source address being that of the system under attack.
The idea is for many systems to reply roughly at the same time, so the attack results in the victim (spoofed source address) being flooded in ping responses.
The process of the attack can be outlined as follows and a graphical representation is given in Figure 8:
1. The attacker forges a ping packet with the source address set to that of the target system (e.g. 192.168.123.45)
2. The forged ping packet is sent to the broadcast address of remote networks (e.g. 10.0.0.255)
3. Pinging the broadcast address causes all hosts on that network to respond to the forged ping request.
4. The hosts on the remote network each return pings to the target host, flooding it with pings.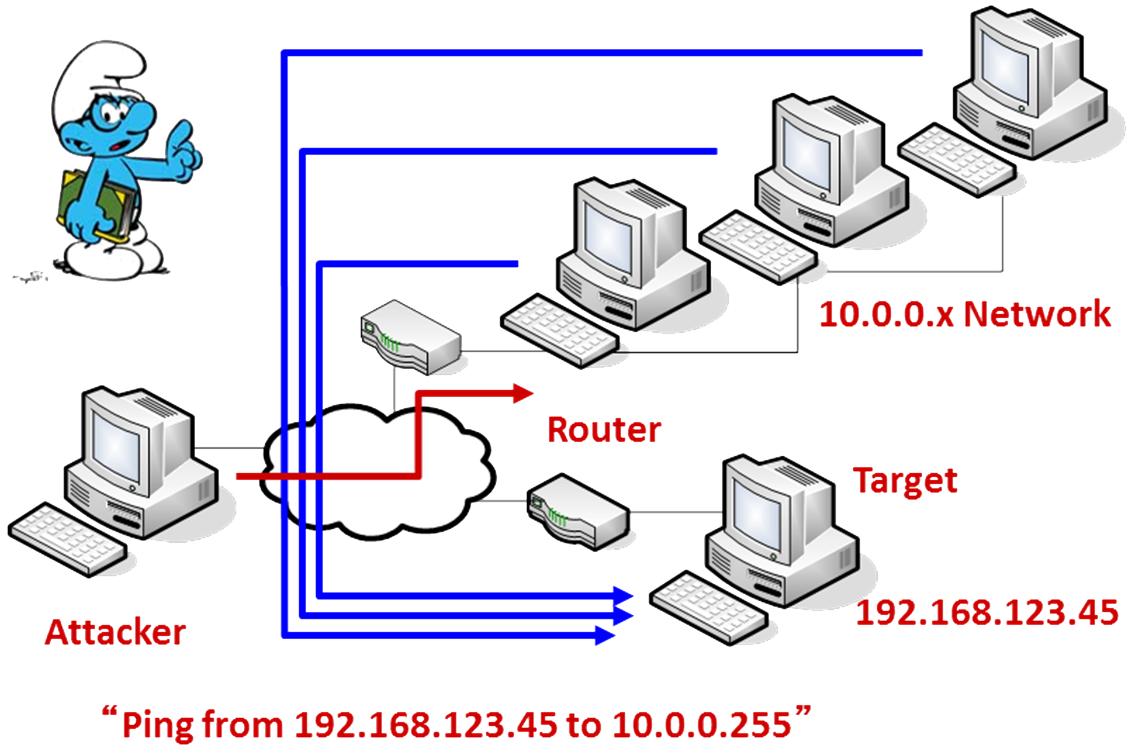
Figure 8 - Smurf Attack While nowadays the Smurf attack is largely ineffective (as many routers and network devices are capable of stopping it) it is a good example of an amplification DoS attack (probably the first). That is an attack that could be launched with relatively low bandwidth to disable a system with higher bandwidth by amplifying traffic.
A much more modern example of an amplification attack uses DNS and is explained below.
DNS Amplification Attack
A DNS amplification attack is also known as DNS reflection attack as it uses DNS servers to “reflect” and amplify traffic and direct it against a specific target. This is a fairly modern example of a distributed denial of service (DDoS) attack.
Here is how it works. An attacker spoofs DNS requests to several name (DNS) servers directing the response to the target. Through various techniques, which are explained in the reference given, the attacker turns a small DNS query into a much larger response directed at the target network. For this to work the DNS server must be misconfigured. However, there are a large number of those on the Internet and they are called Open DNS resolvers. Basically they are DNS servers that accept queries from any client and reply to them.
The original request is often relayed through a botnet for a larger base of attack and further concealment. The amplification used on this attack can increase the size of the requests from around 40 bytes to above the maximum Ethernet packet size of 4000 bytes. This requires packets to be broken down for transmission and then reassembled, requiring further target network resources.
A botnet could send a vast number of these requests enabling an attacker to direct a large amount of traffic to their intended victim.
The attack is difficult to defend from as it comes from valid DNS servers. One of various projects is aiming at defending against these attacks by reducing the number of misconfigured DNS server.
-
Access attacks
Remote exploit
An exploit attack is basically a software tool designed to take advantage of a flaw in the system. The attacker attempts to gain access to a system and gain control. This type of attack is often followed by other attacks such as privilege escalation, passwords attacks and/or malware.
We will experiment with one example of these attacks in the lab, by using Metasploit to launch an attack against the servers in our test topology.
SQL Injection
SQL stands for Structured Query Language and is used to query database systems including Microsoft SQL Server, Oracle and MySQL. The use of SQL is mostly consistent across all versions of databases that support it.
A SQL injection attack is a type of attack that takes advantage of flaws within the SQL language itself. It involves the modification of SQL statements used within a web application. Insufficient user input validation and allowing unchecked improper SQL statements in web applications could result in an attacker performing an SQL injection attack.
An SQL attack can have various results including access to a system, data theft and/or modification, remote command execution, etc..
SQL injection is so popular and such a potentially destructive attack, that the Open Web Application Security Project (OWASP) makes it the number one threat to web applications.
Cross-Site Scripting
Cross-Site Scripting (XSS) is an input validation issue that lets attackers run scripts in a browser within the context of a site that is being viewed. This amongst other things can result in sending authentication cookies to a malicious user.
A simplified example would see a user visiting a web site (often following a phishing attack), which, thanks to some interaction, sends a script to the user machine. This is automatically launched by the victim’s browser and could result in several malevolent actions.
Similar to a SQL Injection attack, preventing this attack involves filtering user input.
-
Other types of attacks
Many more types of attacks exist. The list can be long and covering them all is practically not possible. A simple explanation of some other forms of attacks is given next.
Eavesdropping
As the name suggests, eavesdropping indicates secretly listening to a communication between devices in a network. Ettercap is one of the tools which could be used for this type of attack.
Privilege Escalation Attack
A privilege escalation attack is an attack which aims at elevating access to a system or network. This type of attack is often used in conjunction with a remote access attack. Whenever an attacker gains access they may not have administrator rights required to perform some actions. Therefore a successful privilege escalation attack allows an attacker to obtain admin right for a system.
Spoofing
Spoofing is an attack which allows a person or a program to impersonate another by modifying some data in an exchange. This could be either an IP address, and email address and much more.
-
References & Further Readings
[1] – National Cyber Security Centre (NCSC), Mitigating Denial of Service (DoS) Attacks. Available at: 🔗 https://www.gov.uk/guidance/mitigating-denial-of-service-dos-attacks
[2] – ISGMLUG, ICMP Protocol Exploit – Loki, 2014. Available at: 🔗 http://isgmlug.org/2014/01/31/icmp-protocol-exploit-loki/
[3] – M. Rouse, DNS amplification attack, Whatis.com,2013. Available at: 🔗 http://whatis.techtarget.com/definition/DNS-amplification-attack
[4] – M. Rouse, Definition of Ping of Death, Whatis.com, 2006. Available at: 🔗 http://searchsecurity.techtarget.com/definition/ping-of-death
[5] – M. Prince. Deep inside a DNS Amplification DDoS attack, CloudFare, 2012.Available at: 🔗 https://blog.cloudflare.com/deep-inside-a-dns-amplification-ddos-attack/
[6] – Open Resolver Project. Available at: 🔗 http://openresolverproject.org/
[7] – Cisco, Understanding SQL Injection. Available at: 🔗 http://www.cisco.com/c/en/us/about/security-center/sql-injection.html