-
Web Application Technologies
There are many different technologies, architectures and configurations available when selecting a web application deployment.
Application Architecture
Web applications are generally built using a multi tiered architecture. For the purpose of this module a four-tier representation is used.
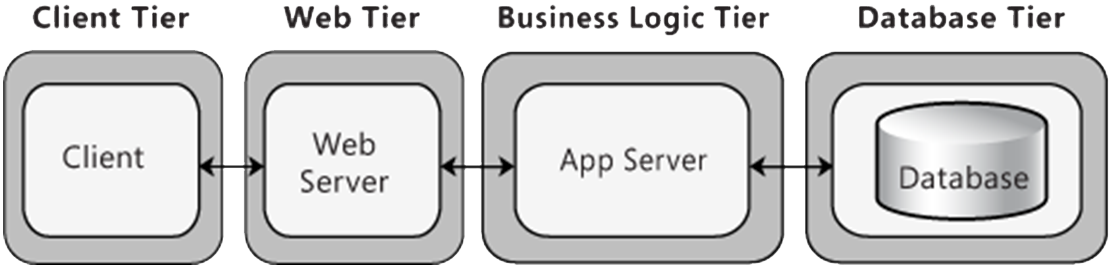
The Front End / Presentation Server
The presentation server is the component responsible for receiving requests from the user and serving pages to be rendered within the browser. For websites that do not host any dynamic content a presentation server can be used in isolation since no further processing is required.
The HTTP protocol is used to communicate with the presentation server; this protocol is examined in detail later in this section.
The most popular web servers (Presentation Servers) are Apache from the Apache Software Foundation and Internet Information Server (IIS) from Microsoft. Several other platform exist, such as Zeus and Apache variants.
-
Server Side Processing
The majority of web applications provide some form of dynamic or interactive content. This can range from a “contact us” style email submission form to a full feature ecommerce offering.
The “Server Side Processing” tier provides application processing such as the processing user supplied content, database interaction and communication with out bound systems.
Most application vulnerabilities are due to coding error at Server Side Processing level.
Common server side scripting languages include:
The Java Server Platform
The platform is a popular choice for large-scale enterprise deployments. The most common java deployment is the “Java Platform Enterprise Edition” formally known as J2EE.
The Java Platform can run on most common operating systems such as Windows, Linux and Solaris (among other Unix Variants).
The java platform is modular by design and lends itself well to multi-tiered and load balanced architectures.
ASP .NET
ASP .NET is Microsoft’s web application framework and competitor to the Java Platform. ASP .NET uses the same .Net framework used in many Windows desktop applications to provide a virtual machine and a set of powerful API’s. The ASP .NET architecture supports all .NET programming languages such as C#, VB and Jscript.
ASP .NET application are generally developed within the Microsoft Visual Studio development environment which offers familiarity to developers of “Fat” client applications and an ideal starting point for novice programmers.
Microsoft has taken a proactive approach to security over the past few years and as a result has included some proactive measures such as Cross Site Scripting protection within the ASP .NET framework.
ColdFusion
ColdFusion is an application framework developed by Adobe. The primary distinguishing feature of ColdFusion is its associated scripting language, ColdFusion Markup Language (CFML), which compares to JSP, ASP .NET, or PHP and resembles HTML in syntax.
PHP
PHP is a free web application programming language and framework that has often been the first choice for beginners. PHP has a long history and has been used to develop several popular open source projects such as the popular bulletin board systems “PHPBB” and PHP-Nuke.
The PHP platform has historically made it easy for programmers to unwittingly introduce security flaws into their code. Several PHP specific bugs exist which are well publicised.
Data Tier
The data tier provides the data storage and database functionality. Elements of the data tier can also be represented under the “Server Side Processing” header due to the fact that data is often manipulated by the database server.
The HTTP Protocol
It is important to understand how the client browser interacts with your web applications from a detailed technical perspective. This section provides an analysis of the HTTP, Server Response headers, and browser interaction methods.
The Hyper Test Transfer Protocol (HTTP) is the core communication protocol used to access content over the Internet. HTTP is a Message Based Protocol that operates by sending a request message to the server and receives a response message in return. HTTP was originally implemented to access simple static content and was therefore designed as a stateless protocol. However, HTTP is transported via TCP which maintains the integrity of the transmission and has the ability to maintain state via a number of application specific methods such as session IDs.
HTTP Requests
HTTP Requests are constructed with a request line, several headers, an optional message body, and a mandatory blank line. There are two primary types of HTTP request implemented for browsing and interacting with the web application; GET and POST. In the most basic form, GET requests are generated by following links or typing a URL into the browser address bar and POST requests are generated by submitting forms. Requests can also be submitted by client side components such as JavaScript and Shockwave Flash components.
-
GET Requests
The following request is generated by entering http://www.sec-1.com/index.htm into the address bar within Windows Internet Explorer 7.
HTTP GET Request 1 GET /index.htm HTTP/1.1 2 Accept: */* 3 Accept-Language: en-gb 4 Accept-Encoding: gzip, deflate 5 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0, Windows NT 6.0) 6 Host: www.sec-1.com 7 Connection: Keep-Alive 8 Cookie: ASP .NET_SessionID=xxxxxx 9 Several other HTTP request methods exist such as HEAD, OPTIONS and PUT. However these methods are typically implemented to interact with the web server and upload content rather than the web application.
HTTP GET Request Analysis 1 The first line of the HTTP request comprises of the HTTP request method which is typically either GET or POST followed by the required resource and the HTTP version (either HTTP/1.0 or HTTP/1.1 at the time of writing) 2-4 Accept-* headers are used to inform the server to which methods of encoding, compression and content types are supported by the client. These headers are optional and are often ignored depending on the type and configuration of the application/presentation server. 5 The User-Agent header is set by the client browser to identify itself to the application. Developers and third party products will often use the User-Agent header to provide browser specific content such as differentiating between a desktop browser to that of a portable device. 6 The host header informs the server which host name the user is requesting resources from. Main stream web servers such as IIS and Apache will permit more than one website to be hosted from a single IP address. The server will then use the host header to identify which server the client is attempting to access. This method of hosting multiple web servers is referred to as virtual hosting. 7 Connection headers instruct the web server to either keep the connection alive or close it after the current transaction. 8 The cookie. Cookies are covered in detail later 9 The mandatory blank line (CR LF) HTTP Requests can include many more headers and variations depending on the client, request type and any additional software such as a browser plug in.
-
POST Request
POST Requests are sent to the application as a result of submitting a HTML form, as a result of a Client Side Script (e.g. JavaScript, Shockwave) or as part of an Ajax interaction.
The following POST request was generated by submitting the following HTML form:

HTML form code
<form action = ‘/process_login2.asp’> Username: <input type=’text’ name =’username’><br/> Password: <input type=’password’ name =’password’> <input type=’submit’ value =’login’>
HTTP POST Request 1 POST ‘/process_login2.asp’> 2 Accept: */* 3 Accept-Language: en-gb 4 Accept-Encoding: gzip, deflate 5 Referer: http://192.168.0.197/ 6 Content-Type: application/x-www-form-urlencoded 7 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0) 8 Host: www.sec-1.com 9 Content-Length: 32 10 Cookie: ASP .NET_SessionId=xxx 11 12 Username=gary&password=hacker123 HTTP POST Request Analysis 1 The first line of the HTTP request comprises of the HTTP request method which is typically either GET or POST followed by the required resource and the HTTP version (either HTTP/1.0 or HTTP/1.1 at the time of writing) 2 - 4 Accept-* headers are used to inform the server which methods of encoding, compression and content types are supported by the client. These headers are optional and are often ignored depending on the type and configuration of the application/presentation server. 5 The Referrer header can be present in both GET and POST requests and contains the address of the page where the current request originated from, E.g. if a link on page A is followed to page B, the Referrer header within the request to page B contains the address of page A. 6 The Content-Type header details the content type of the request body. 7 The User-Agent header is set by the client browser to identify itself to the application. Developers and third party products will often use the User-Agent header to provide browser specific content such as differentiating between a desktop browser to that of a portable device. 8 The host header informs the server which hostname the user is requesting resources from. Mainstream web servers such as IIS and Apache will permit more than one website to be hosted from single IP address. The server will then use the host header to identify which server the client is attempting to access. This method of hosting multiple web servers is referred to as Virtual Hosting. 9 The Content-Length header details the length of the request body in bytes. The server will read to the end the request body based upon this value and then drop the connection. 10 The cookie. Cookies are covered in detail later 11 The mandatory blank line (CR LF) 12 The request body -
PUT Request
PUT Requests are implemented to upload content to a web server. Permitting this type of request is not recommended since it could be abused by an attacker to upload malicious content to the web server. The following PUT request attempts to upload a file named “text.txt” containing the string “Hello World” into the web root.
HTTP PUT Request 1 PUT /test.txt HTTP/1.1 2 Host: www.sec-1.com 3 Content-Length: 11 4 5 Hello world 6 The request headers here have the same meaning as POST headers described previously.
OPTIONS Request
The OPTIONS method requests a list of valid request methods for the given directory. The following request will display a list of valid methods for the root directory, providing the OPTIONS method has not been restricted.
HTTP OPTIONS Request 1 OPTIONS / HTTP/1.1 2 Host: www.bbc.co.uk 3 Example Response
HTTP/1.1 200 OK Date: Wed, 30 April 2008 10:19:46 GMT Server: Apache/2.0.59 (Unix) Allow: GET, HEAD, POST, OPTIONS, TRACE
HEAD Request
The HEAD request method operates in a similar way to GET but does not return a page body. HEAD is typically used when client wants to determine the content type and length of the request before downloading it.
TRACK / TRACE Request
The TRACK and TRACE methods are used for diagnostic purposes. Requests formed with these methods should respond with the exact same values held within the request. From a security perspective it may be possible to abuse the TRACK and TRACE methods to perform cross site scripting attacks. However, most modern browsers have been patched to prevent this.
-
HTTP Responses
The web server/application will respond in a number of different ways to each request. The following status code groups provide an indication of how the request was received.
Group Description Code Details 1xx Informational 100 Continue
This code indicates that the headers have been received and informs the client to continue sending data2xx Successful 200 OK
Indicates that the request was received successfully and the response body contains the result of the request 201 Created
A 201 response indicates that an attempt to upload a file to the web server via a PUT request was successfulGroup Description Code Details 3xx Redirection 301 Moved Permanently
A 301 indicates that the page has moved to the address held within the Location header. Most browsers will automatically redirect to this location. 302 Found
A 302 indicates that the page has temporarily moved to the address held within the Location header. Most browsers will automatically redirect to this location. 302’s will often occur as part of application logic. For example, selecting a particular language option may result in a 302 to a regional version of the web application. 304 Not Modified
This instructs the browser to use a cached copy of the resource if available.Group Description Code Details 4xx Access Error 400 Bad Request
The server did not understand the request. This is generally due to a malformed request path such as white space in request to IIS. 401 Unauthorised
The requested resource cannot be accessed without authentication. The WWW-Authenticate header contains the accepted authentication types. 403 Forbidden
Access to the resource is forbidden. No further authentication options are available. 404 Not Found
The resource cannot be located 405 Method Not Allowed
A 405 response code indicates that the request method for the specified resource is not valid. This can occur when dangerous request methods such as PUT have been disabled. 413 Request Entity Too Large
This response indicates that a string within the request has exceeded an acceptable limit. 414 Request URI Too Long
This response indicates that a string within the requested resource has exceeded an acceptable limit.5xx Server Error 500 Internal Server Error
A 500 status code indicates that there has been an error with server side processing. This error will often occur when a server side script has thrown an error due to malformed input. 503 Service Unavailable
This error can occur when a resource has been overwhelmed or has become an available due to an integrated failure.The following is an example of response to a standard GET request as detailed above.
GET Request: 200 OK Response:
HTTP Response 1 HTTP/1.1 200 OK 2 Date: Tue, 29 Apr 2008 13:46:00 GMT 3 Server: Microsoft-IIS/6.0 4 Set-Cookie: ASP.NET_SessionId=xxx; path=/; 5 Cache-Control: private 6 Expires: Tue, 29 Apr 13:45:00 GMT 7 Content-Type:text/html; charset=utf-8 8 Content-Length:34905 9 10 <PAGE BODY: 34905 Bytes> HTTP Response Analysis 1 The first line of the response details the HTTP version in use, the HTTP response code and a textual representation of the response status. In this case the response is “200 OK” message meaning that the request was received and corresponding resource was located 2 The date header 3 This server header is returned by default and contains a string representing the presentation server (web server) type and version. Server headers are useful when planning an attack against a web server. Some web servers administrators will configure their web servers to respond with misleading header or remove it altogether. Whilst this does provide some level of obscurity there are several other methods available when finger printing the web server type and version. 4 `the Set-Cookie header instructs the browser to store a cookie for the specified path.
Cookies are covered later.5 Cache-Control header passes caching directives to the browser to instruct it on how to cache content. For further information regarding Cache directives please see: 🔗 http://www.w3.org/Protocols/rfc2616/rfc2616-sec14.html#sec14.9.1 6 The Expires header dictates how long the contents of the message body are valid for. This is implemented to instruct the browser cache to expire the content after the defined date. 7 The content type header specifies the content-type of the message body. The client browser uses this header to select a component to render the content. 8 Content-Length specifies the length of the message body in bytes 9 Mandatory Blank Line 10 The Message Body