-
Web Application (In)security
The most serious attacks against the web are those that expose sensitive data or gain unrestricted access to backend systems on which the application is running. Web application security is today the most significant battleground between hackers and those with computer resources and data to defend. The majority of applications are insecure, despite the use of SSL technology and the adoption of PCI scanning.
Some of the Types of Vulnerabilities
Broken authentication
Broken access control
SQL Injection
Cross-site scripting
Information leakage
-
SSL Myth
Unfortunately there is a myth out there that if one uses SSL that makes them secure. SSL is an excellent technology that protects the confidentiality and integrity of data in transit. It helps defend against eve droppers. It can provide assurance to the user of the identity of the web server they are dealing with.
Unfortunately SSL does not stop attacks that directly target the server nor client components of an application as most successful applications do. It does not prevent any of the above vulnerabilities, or many others that can render an application critically exposed to attack. Regardless of whether they use SSL, most web applications still contain security flaws.
Core Security Issues
The core security problem is that: users can submit arbitrary input. The server side application must assume that all user/client input is potentially malicious. The server side must take steps to ensure that attackers cannot use crafted input to compromise the application by interfering with its logic and behaviour. Users can interfere with any data exchanged between the client and the server.
As a developer you also need to know that users can send requests in any sequence not the one you assume they would. Users are not restricted to using only a web browser to access applications, they can use other applications such as curl. The majority of attacks against web apps involve sending input to the server that is crafted to cause some event that was not expected.
Examples
Changing the price of a product transmitted in a hidden HTML form field or the modification of a session token transmitted in a HTTP cookie to hijack the session.
Hidden fields do not affect the appearance of the page that is presented to the user. Instead, they store fixed names and values that are sent unchanged to the server, regardless of user input. The user can modify the number of items ordered, but there is no visible form element that stores the item ID.
SSL To the Rescue?
Unfortunately not: SSL will not help except ensuring other users on the network cannot view or modify the attackers data in transit. Because the attacker controls her end of the SSL tunnel, she can send anything she likes. From an attacker’s point of view SSL is good because it ensures that the payload is encrypted which means it can evade any mitigation measures which cannot deal with encrypted data.
Key Problem Factors
Several factors have combined to exacerbate the security problems. These factors explain why so many web applications on the Internet have been compromised.
One of the main issues is the under developed security awareness. The essentials of security, networks and hardening of hosts is well understood but widespread confusion still exists about core concepts involved in web application security. We have focused a lot on perimeter security at the expense of end point security.
Today, web application development involves weaving together several third party packages. The packages are designed to abstract the developers away from the underlying technologies. This is good in terms of removing complexity and making the technology widely accessible but very bad for understanding the underlying technologies.
Some web application developers make major assumptions about security provided by these widespread programming frameworks. The abstraction introduces deceptive simplicity in custom developments. It is possible for novice programmers to create complex and powerful applications without understanding the security implications of the different components that they have weaved together.
The other issue is that the technology landscape is changing very fast which means the security threat landscape is also rapidly evolving. New vulnerabilities are discovered and announced everyday.
The other constraint is that of resource and time. Every development team that we know of is under resourced. The users are always pushing for more features and fast releases. These increased demands on functionality may lead to compromises in security.
The other issue is that of over extended technologies. Most of the technologies in use today are being used in ways that they were never imagined when they were developed.
The Future of Web Application Security
The first step is a good understanding of the security threats facing web applications. This is then followed by developing effective ways of addressing them which are still under developed currently.
There is need for a realization that attention is shifting from attacks against server side to attacks targeting application users. Attacks will still leverage defects within the application.
-
Core Security Concepts
Vulnerability – a weakness or flaw that may provide an opportunity to a threat agent
Threat Agent – an entity that may act on vulnerability
Threat – any potential danger
Risk – the likelihood of a threat agent exploiting a discovered vulnerability
Exposure – an instance of being compromised by a threat agent
Countermeasure – an administrative operation, or logical mitigation against potential risks
CIA Triangle
If you are developing an application or service online then the service and the data should be wrapped around the so-called CIA triangle. This is what you should guarantee on the minimum. CIA stands for Confidentiality, Integrity and Availability
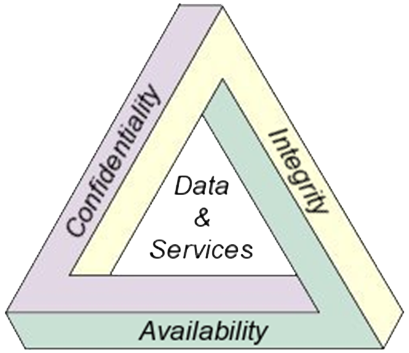
Confidentiality is the concept of preventing the disclosure of information to unauthorized parties. It is about viewing data. Not only does confidentiality assure the secrecy of data but it also can help in maintaining data privacy.
Integrity is the concept of protecting the data from unauthorized alteration. It has two aspects: Firstly, it must ensure that the data that is transmitted, processed and stored is as accurate as the originator intended and secondly, the software performs reliably as it was intended to.
Availability is the security concept that is related to the access of the software or the data or information it handles. What sort of actions support availability? It is determined by the criticality of the data or service and its purpose in the system. Load balancing, replication and disaster recovery are mechanisms that can be used to ensure availability
Authentication is the process of determining the identity of a user
- Three general methods are used in authentication. In order to verify your identity, you can provide:
- Something you know (password, pin)
- Something you have (token, e.g. phone)
- Something you are (something about you, i.e. fingerprint (biometric))
Accounting, also known as auditing. It is a means of measuring activity
This can be done by logging crucial elements of activity as they occur in an application. Audit logs are a balancing act as they require resources to create, store and review.
NonRepudiation is the concept of preventing a subject from denying a previous action with an object in a system. When authentication, authorisation and auditing are properly configured, the ability to prevent repudiation by a subject with respect to an action and an object is ensured.
- The State of Application Security
- “75% of all attacks are now aimed at the application layer while 90% of security dollars are spent on network layer” – Gartner Report
- ‘92% are application vulnerabilities instead of network vulnerabilities’ – NIST
- “The battle between hackers and security professionals has moved from the network layer to the applications themselves” – Network World
- “64% of application developers are not confident in their ability to write secure applications” – Microsoft, Development Research
- ‘Hacking has moved from a hobbyist pursuit with a goal of notoriety TO A CRIMINAL pursuit with a goal of money” – Counterplane Internet Security
- Examples of Common Attackers (and why)
- Hackers (to vandalise or steal $$)
- Terrorists (Disrupt operations)
- Foreign Governments (steal proprietary information)
- Competitors (steal proprietary information)
- Malicious Employee (Disrupt operations)
- Unaware Employees
The hackers’ industry is very motivated as you can see from above. They are very organised with sophisticated tools and frameworks. It is a well-developed industry. Hackers can fail many times with no downside. We the defenders of applications cannot afford to fail once because every security breach is one too many. We will now start talking about how to design and develop applications with security in mind.