-
Mobile Devices – Smart Cards and Tags
- Examples of modern devices are:
- Calculator (primitive, but truly mobile computing!)
- A myriad of devices available today, which can be classed in four main categories:
- Information Access
- Intelligent Appliances
- Smart Controls
- Entertainment Systems
Information Access Devices
PDAs also called “palm-tops”, as their size is roughly that of a human palm, were the once dominant “species” in this category, now the smartphone. Users of these devices are able to connect to networks or other devices and carrying personal information (calendar, address book, messages), allowing information to be easily accessible and available when needed. The difference between smartphone and PDA is now very blurred.
Handheld Devices have specialist applications and may need to be “ruggedized”. Here are examples of handheld devices:

MC3200 Mobile 
Unitech EA600 Smart Identification
People and objects need to communicate in the “pervasive computing landscape”. Computer systems need to track people, objects etc. This can be accomplished by using smart tags in ordinary objects e.g. cards, paper labels, keyrings, etc.
Smart Cards
One of the most common device is a smartcard. A smartcard is a plastic card that contains an embedded computer chip that stores and transacts data. Can be used as SIM card, health care card, payment card, ID card, e-wallet etc.
X X
X
-
Types of Smart card
Smart cards are defined according to how the card data is read and written and the type of chip implanted within the card and its capabilities. Smart cards contain either a Memory chip or Microprocessor.
- Memory chip
- Cannot manage files and have no processing power for data management.
- Cannot manage files and have no processing power for data management.
- They are less expensive than microprocessor chips, but they also offer less security so they should not be used to store sensitive or valuable information.
- Microprocessor chip
- Manages this memory allocation and file access.
- An "intelligent" controller used to securely add, delete, change and update information contained in memory.
- The more sophisticated microprocessor chips have state-of-the-art security features built in to protect the contents of memory from unauthorized access.
Types of Smart card

As previously discussed there are different types of smart card, most common are:
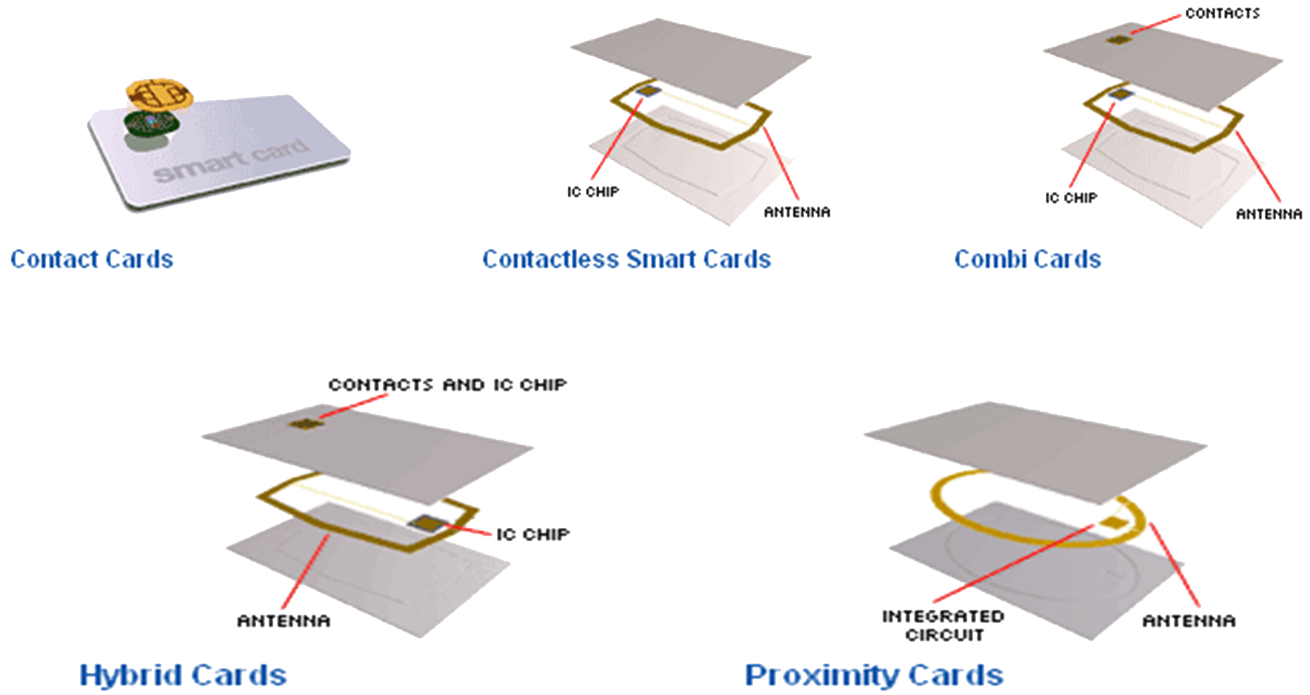
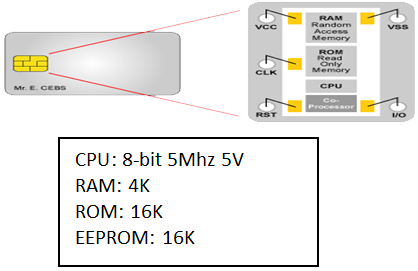
- Smartcard Hardware
- ISO7816 (ISO02)
- CPU (8/16/32-bit)
- Co-processor (cryptography)
- RAM
- ROM (O/S, Comms, Security)
- EEPROM (Filesystem, Program Files, Keys, Passwords, Applications)
- Smartcard Readers
- Readers attached to PC (serial/USB)
- Integrated in keyboard
- Embedded into appliances (ATM)
- Mobile phones
- Set-top boxes
- P.O.S. equipment
-
- Smart Labels (Barcode)
- Combining human-readable information and bar code technology.
- Consists of an adhesive label.
- Line-of-sight.
- Can only be read one at a time.
- Static.
- Unable to be rewritten.
Example of smart labels (Barcode)
A. Routing Code: This code tells us how to route a package within a UPS building.
B. Postal Bar Code: The linear version features the zip code for the package's destination.
C. Service Icon: This symbol indicates the package level of service (1DA, 2DA etc.) without reading any other text on the label.
D. MaxiCode: This machine-readable code can be understood regardless of its direction. It uses 2 symbology for such information as postal code, country code, service class (1DA etc), tracking number, Julian date, package quantity and weight, address validation, and ship street, city and state.
E. 1Z tracking number: This code lets a customer follow a package as it moves through our system. A 1Z tracking number identifies the customer shipper number, package service level, and customer reference number.
Another example of smart labels (Barcode)

Smart Labels (Barcode) pros and cons
- Cons
- Must be visible
- short range
- object separation
- read-only info
- no security
- Pros
- Printable
- Inexpensive
- Reliable
- Scanable.
- etc.
-
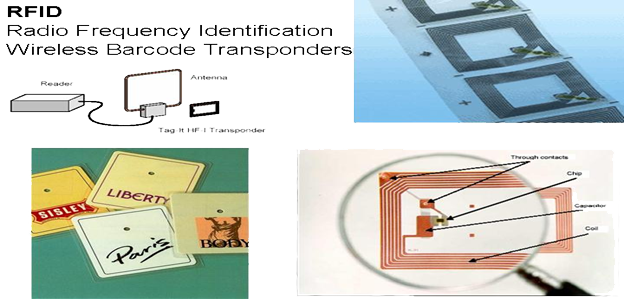
Radio Frequency Identification
- RFID tags consist of an integrated circuit (IC) attached to an antenna (typically a small coil of wires) plus some protective packaging (like a plastic card). Sometimes known as transponders or inlays. Technically an inlay is a tag mounted on a substrate that is ready to be converted into a smart label. Here’s some characteristics of radio frequency identification:
- Can come in many forms and sizes.
- Can be as small as a grain of rice.
- Data is stored in the IC and transmitted through the antenna to a reader.
- RFID tags are either passive (no battery) or active (self-powered by a battery).
- Tags can be read-only (stored data can be read but not changed), read/write (stored data can be altered or rewritten), or a combination, in which some data is permanently stored while other memory is left accessible for later encoding and updates.
- Radio Frequency Identification – how does it work
- Information is sent to and read from RFID tags by a reader using radio waves.
- Passive systems, (most common), an RFID reader transmits an energy field that "wakes up" the tag and provides the power for the tag to respond to the reader.
- Active systems, a battery in the tag is used to boost the effective operating range of the tag and to support additional features.
- Data collected from tags is then passed through communication interfaces (cable or wireless) to host computer systems.
-
Radio Frequency Identification - What is it?
So, Radio Frequency Identification provide real-time, wireless transmission of data without human intervention which do not require line-of-site scanners for operation. Allow stored data to be altered during sorting or allow workflow process information to be captured with the data and work effectively even in harsh environments with excessive dirt, dust, moisture, and extreme temperatures.
Smart Labels (RFID) – how does it work
Smart labels work by combining human-readable information and bar code technology with Radio Frequency Identification (RFID) and consists of an adhesive label that is embedded with an ultra-thin RFID tag "inlay" which is a tag-IC plus antenna-mounted on a substrate. It works by combines the read range and unattended processing capability of RFID with the convenience and flexibility of on-demand label printing.
Smart Labels (RFID) – What is it?
Smart labels (RFID) can be pre-printed and pre-coded for use in on-demand applications, the tag inlay can be encoded with fixed or variable data and tested before the label is printed and the label can retain all existing formats and layouts that are required to support bar codes, text, and graphics used in established applications. A read/write smart label also can be programmed and reprogrammed in use, following initial coding during the label production process.
Further examples of Smart Labels (RFID)
-
RFID Communication
Low-frequency RFID systems (30 KHz to 500 KHz) have short transmission ranges (generally less than six feet).
High-frequency RFID systems (850 MHz to 950 MHz and 2.4 GHz to 2.5 GHz) offer longer transmission ranges (more than 90 feet).
So in general, the higher the frequency, the more expensive the system. Data Transfer rates in the range < 1kbit/s to 100kbits/s. Tag collision happens when multiple tags are energized by the RFID tag reader simultaneously, and reflect their respective signals back to the reader at the same time. This problem is often seen whenever a large volume of tags must be read together in the same RF field. The reader is unable to differentiate these signals, and that is because tag collision confuses the reader.
However, different systems have been invented to isolate individual tags, so the system used may vary by vendor. For example, when the reader recognizes that tag collision has taken place, it sends a special signal (a "gap pulse"). Upon receiving this signal, each tag consults a random number counter to determine the interval to wait before sending its data. Since each tag gets a unique number interval, the tags send their data at different times. For example, table below shows RFID Communication operating frequencies and its associated characteristics.
Table 2: RFID operating frequencies and associated characteristics. Band LF Low frequency HF High frequency UHF Ultra high frequency Microwave Frequency 30 - 300 kHz 3 - 30 MHz 300 MHz - 3 GHz 2 - 30 GHz Typical RFID Frequencies 125 - 134 kHz 13.56 MHz 433 MHz or
865 - 956 MHz
2.45 GHz2.45 GHz Approximate read range less than 0.5 metre Up to 1.5 metres 433 MHz = up to 100 metres
865 - 956 MHz = 0.5 to 5 metresUp to 10m Typical data transfer rate less than 1 kilobit per second (kbit/s) Approximately 25 kbit/s 433 - 956 = 30 kbit/s
2.45 = 100 kbit/sUp to 100 kbit/s Characteristics Short-range, low data transfer rate, penetrates water but not metal. Higher ranges, reasonable data rate (similar to GSM phone), penetrates water but not metal. Long ranges, high data transfer rate, concurrent read of < 100 items, cannot penetrate water or metal Long ranges, high data transfer rate, cannot penetrate water or metal Typical use Animal ID
Car immobiliserSmart labels
Contact-less travel cards
Access & SecuritySpecialist animal tracking
LogisticsMoving vehicle toll -
RFID Communication Problems
- There are some technical problems in RFID Communication such as:
- Problems with RFID Standards
- RFID systems can be easily disrupted
- RFID Reader Collision
- RFID Tag Collision
RFID Security
The contents of an RFID tag can be read after the item leaves the supply chain. RFID tags are difficult to remove and it can be read a greater distance with a high-gain antenna so can be read without your knowledge. RFID tags with unique serial numbers could be linked to an individual credit card number.
Sources

Smart Card Basics,
🔗 http://www.smartcardbasics.com/smart-card-overview.html
