03
-
Introduction
- his week you will continue to learn about a range of issues that are important to Computing professionals. These are issues that you need to be aware of in your future career. You will also need to consider, later in the module, which issues may apply to the topic which you choose for your project proposal.
- This week we will look at the following:
- Legal Issues – privacy, intellectual property, risk and liability
- The nature of a Profession
- Professional bodies
- Codes of conduct
- Standards
-
Privacy
- Information is valuable but can also be a liability. It is important to ensure that private information relating to persons or institutions does not become public without consent.
- The demand for information, and hence the importance of privacy in relation to that information, has been driven by:
- Increasing digitization of information
- Declining costs of digital communication
- Increased miniaturization of mobile computing devices and other communications equipment
- Greater public awareness of the potential abuse of digital communication
- Elements of privacy:
- Solitude: The right to be alone without disturbances
- Anonymity: The right to have no public personal identity
- Intimacy: The right not to be monitored
- Reserve: The right to control one’s personal information including the methods of dissemination of that information.
- Types of Privacy
- Although there are varied definitions of privacy, the several types of privacy we are going to discuss here are not influenced by the factors we have outlined in the previous section.
- Personal Privacy
- Prevention of anyone or anything that would intrude or violate personal space where those attributes are, including physical searches, video recording, and surveillance
- Informational Privacy
- Concerns the protection of unauthorized access to information, including:
- Personal information, e.g. religion, sexual orientation, political affiliations, or personal activities
- Financial information
- Medical information
- Institutional Privacy
- Privacy of data which is critical to business, e.g. research data, sales and product data, marketing strategies
- Privacy protection
- Technical
- Through the use of software and other technically based safeguards and also by education of users and consumers to carry out self-regulation.
- Contractual
- Contractual protection against unauthorized reproduction or distribution - needs to be enforceable.
- Legal
- Through the enactment of laws by national legislatures and enforcement of such laws by the law enforcement agencies. For example, the European Union has recently introduced the General Data Protection Regulation (GDPR), which is the most important change in data privacy regulation in that region in 20 years.
-
Intellectual Property
- Creating or providing computer technology products, services, and software requires a considerable investment in both time and money. So the individuals who do this work should reap financial rewards for their efforts. This creativity must therefore be protected
- Intellectual property rights form a wide scope of mechanisms that include copyrights, patents, trademarks, protection of trade secrets, Unfortunately, some of these laws are not universal; they only apply in one country. And even within the USA, the same laws may not apply in all states. In particular, we look at intellectual property rights as they apply to computer products, services, and software.
- Copyrights
- Copyright is a right, enforceable by law and accorded to an inventor or creator of an expression, which is an original work that has a tangible form and is fixed in a medium - can include creative works together with audiovisual and architectural works and sound recordings.
- Patents
- Patents protect inventions or discoveries.
- Trade Secrets
- A trade secret is information that gives a company or business a competitive advantage over others in the field. It may be a formula, a design process, a device, or trade figures. Thus, there is no one acceptable description or definition of trade secrets.
- Trademarks
- A trademark is a label that identifies a product or service, and attempts to distinguish itin the minds of the consumers. The label may be any word, name, picture, or symbol.
- Fair Use Doctrine
- Establishes a balance between the protection of rights of content owners to benefit from their works and the basic rights of the community to gain from each member’s contributions for the betterment of all. The use of copyrighted material is considered fair if it does not exploit the commercial value of the work.
- There are four ways to judge whether the use of an invention, discovery, or work is fair or not.
- Purpose of use, commercial or educational
- Nature of use
- Percentage of use
- The effect of use on the commercial value of the invention, discovery, or works
- There are so many exceptions and inclusions under the fair use doctrine that it is difficult to be sure what fair use is unless one talks to a copyright lawyer or other experts knowledgeable in copyright law.
- Protecting Computer Software Under IP
- Algorithms and ideas are not classified as intellectual property and, therefore, are not in any way protected. However, software, although it makes use of algorithms, is not considered to be an algorithm but rather a manifestation, an expression of that algorithm.
- Protection of Software under Copyright Laws
- Computer software, along with its documentation, can be protected under the copyright laws. The developer of a program thus has protective rights to authorize others of his or her choice to reproduce the format of the program, to update and upgrade the program and distribute it for free, or to sell or transfer ownership. The buyer of such a program has some protected rights also. The buyer has the right to make another copy as a backup, provided that a copy is not used on another machine. However by registering software for copyright, the developer is opening up the secrets of the whole project, and courts in some countries have taken the position that copyright registration precludes maintaining software as a trade secret.
- Protection of Software under Patent Laws
- Unlike copyright laws, patents protect the processing of the idea; they also protect the implementation of the idea as a machine, a manufacturing process, or a composition of matter or materials. Under these conditions, computer hardware components, by their very nature, are protected under the patent laws. Software also may be protected under the patent laws under certain circumstances. However, issues around patenting software are not fully settled, and it can be very difficult to apply successfully for patents, particularly as much software is created by smaller ventures that lack the resources required to do so.
- Licensing
- Software is usually protected by licences. When a developer licences his or her work, this does not mean giving away any rights. The developer still holds the original copyright (or patent) on that work. What a license does is grant specific permissions for others to use that work.
- Open-source software
- Open-source software is software that is released under open-source licences. These make it easy for others to contribute to a project without having to seek special permission. They also protect the original creator and help to prevent others from claiming the work as their own.
- The terms open-source software and free software mean almost the same thing, but have a somewhat different philosophy. Open-source is related to how software is developed, whereas free relates to a social movement. The Free Software Foundation (🔗 https://www.fsf.org) states that "Free software is software that gives you the user the freedom to share, study and modify it. We call this free software because the user is free."
- There are a number of open-source licences which differ in the conditions they specify, for example:
- The GNU General Public Licence (GPL)
Link 🔗 https://opensource.org/licenses/gpl-2.0.php - The MIT licence
Link 🔗 https://opensource.org/licenses/mit-license.php - The Apache licence
Link 🔗 http://www.apache.org/licenses/ - Digital Rights Management
- Digital rights management (DRM) refers to any scheme that controls access to copyrighted material using technological means. DRM removes usage control from the person in possession of digital content and puts it in the hands of a computer program.
- Digital rights management tries to solve the problem that the ease of distribution of digital content over the Internet has made traditional copyright law obsolete in practice. However, many consumers consider DRM to be overly-restrictive.
-
Risk
- Risk is a potential problem with causes and effects.
- Causes of software risks include:
- Poor software design
- Mismatch of hardware–software interfaces,
- Poor support, and maintenance
- Personnel shortfalls
- Unrealistic schedules and budgets
- Developing the wrong functions and properties
- Developing the wrong user interface
- Continuing stream of requirement changes
- Effects of software risks can include:
- Loss to the customer
- Loss of reputation or harm to society
- Monetary losses
- Legal actions against the seller
- Catastrophic events
- Consumer protection
- Software products may not work as expected because the buyer has unrealistic expectations about the product, the environment in which the product is supposed to work is inadequate, the seller exaggerated the capacities of the software, or the software is simply faulty. Legal protection for the consumer can come from a number of legal frameworks or agreements.
- Buyer and Provider Rights
- Service-Level Agreements (SLA)
- Customer-based SLA: An agreement with an individual customer group, covering all the services they use.
- Service-based SLA: An agreement for all customers using the services being delivered by the service provider
- Multilevel SLA: The SLA is split into the different levels, each addressing different set of customers for the same services, in the same SLA.
- Service Provider–User Contracts
- Express Warranties - affirmation of a fact, a promise, or a description of goods, a sample, or a model made by the seller to the buyer relating to the goods and as a basis for payment negotiations.
- Implied Warranties - enforced by law according to established and accepted public policy.
- Disclaimers
- Producers try to control their liability losses by putting limits on warranties via disclaimers. Through disclaimers, producers preempt lawsuits from buyers by telling buyers in writing on the contracts the limits of what is guaranteed. Whether these disclaimers are recognized in courts depends on a number of factors including the belief that the disclaimers were made in good faith.
-
Being a Professional
- Build Trust: ethical, customer satisfaction, expertise, extra mile
- Communicate effectively : slowly, clearly, attentively, carefully
- Be Generous: praise others, share, say thank you, smile
- Professional bodies, or societies, play a number of important roles, including:
- Establishing codes of conduct for members
- Establishing mechanisms for dissemination of good practice and new developments
- Setting standards for entry to the profession
- Advising governments about matters within the society's area of expertise
- Professional societies may represent members in:
- Different specialisms within a discipline
- Different geographical regions
- The following list includes societies which represent the broad computing profession in a number of regions/countries:
- United Kingdom
- British Computer Society (BCS) - 🔗 www.bcs.org
- Institute of Engineering and Technology - 🔗 www.theiet.org/
- United States of America
- Institute of Electrical & Electronic Engineers (IEEE) - 🔗 www.ieee.org
- Association of Computing Machinery (ACM) - 🔗 www.acm.org/
- India
- Computer Society of India - 🔗 www.csi-india.org
- China
- China Computer Federation 🔗 www.ccf.org.cn
- Brazil
- Brazilian Computer Society - 🔗 www.sbc.org.br
- South Africa
- Institute of IT Professionals South Africa 🔗 https://www.iitpsa.org.za/
- Unaligned
- International Federation for Information Processing - 🔗 www.ifip.org/
- IFIP is a multinational body with representatives in many countries worldwide, including a number of African countries.
- Continuing Professional Development (CPD) Planning Frameworks
- Career Advice
- Mentoring
- Discounted training opportunities
- Formal recognition using post nominals e.g. MBCS, FBCS, FIEEE
Computing Professional Societies
Benefits of Membership
-
Examples of Codes of Conduct
- Professional Competence and Integrity
- only undertake to do work .. .that is within your … competence.
- not claim any level of competence that you do not possess.
- develop your .. knowledge, skills and competence
- ensure that you have the knowledge and understanding of Legislation
- respect and value alternative viewpoints
- reject and not make any offer of bribery or unethical inducement.
- DUTY to Public Interest
- have due regard for other’s public health, privacy, security, wellbeing
- have due regard for the legitimate rights of Third Parties conduct
- your professional activities without discrimination
- promote equal access to the benefits of IT
- DUTY to Relevant Authority
- carry out your …. responsibilities with due care and diligence …. not disclose or authorise to be disclosed, or use for personal gain or to benefit a third party, confidential information
- DUTY to the Profession
- accept your personal duty to uphold the reputation of the profession
- seek to improve professional standards
IEEE Code of Ethics  UK engineering Council
UK engineering Council Statement of Ethical Principles  IET
IETRules of Conduct  Institute of Mechanical Engineers
Institute of Mechanical Engineers Code of Conduct Regulations  Institute of Civil Engineers
Institute of Civil EngineersCode of Professional Conduct  IEEE
IEEECode of Ethics  ACM
ACMCode of Ethics and Professional Conduct  National Society of Professional Engineer
National Society of Professional EngineerCode of Ethics British Computer Society Code of Conduct
-
Why Adopt Standards?
- To transfer ’good practice’
- To benchmark against “good practice”
- To meet contractual demands of clients
- To meet the demands of a certifying body
- To have a political safety net
- To ensure Product & Service integration
- To adhere to requirements of other standards (ISO9000 and similar) or software process improvement initiatives.
- Part 1: Design principles and framework
- Provides design principles for multimedia user interfaces and provides a framework for multimedia design.
- Part 2: Multimedia navigation and control
- Provides recommendations for media control and navigation in multimedia applications. Media control is mainly concerned with functions for controlling dynamic media such as audio or video. Navigation refers to the conceptual structure of the multimedia application and the user's interactions needed in order to move in that structure. It also includes recommendations for searching multimedia material.
- Part 3: Media selection and combination
- Provides recommendations for the selection of media with respect to the communication goal or the task, as well as with respect to the information's characteristics. It also provides guidance for combining different media. It includes recommendations for integrating multimedia components in viewing and reading sequences.
- 1 Introduction
- 2 General Description
- 2.1 Relation to current projects
- Describe the relationship to other projects
- 3 Specific Requirements
- List the specific requirements, with attributes. Subsections may be regrouped around high level functions.
- 3.1 Functional requirements
- 3.2 Performance requirements
- 3.2 Interface requirements
- 3.3 Operational requirements
- 3.5 Resource requirements
- 3.6 Verification requirements
- Instrumentation & Measurement
- Nanotechnology
- National Electrical Safety Code
- Nuclear Power
- Power & Energy
- Power Electronics
- Smart Grid
- Transportation
- Wired & Wireless
- Aerospace Electronics
- Antennas & Propagation
- Batteries
- Communications
- Computer Technology
- Consumer Electronics
- Electromagnetic Compatibility
- Green & Clean Technology
- Healthcare IT
- Software & Systems Engineering
- Industry Applications
Example: ISO 14915
Software ergonomics for multimedia user interfaces — Part 1: Design Principles and framework
European Space Agency: System Requirements Document Structure
IEEE Standards Themes
-
Developing Standards
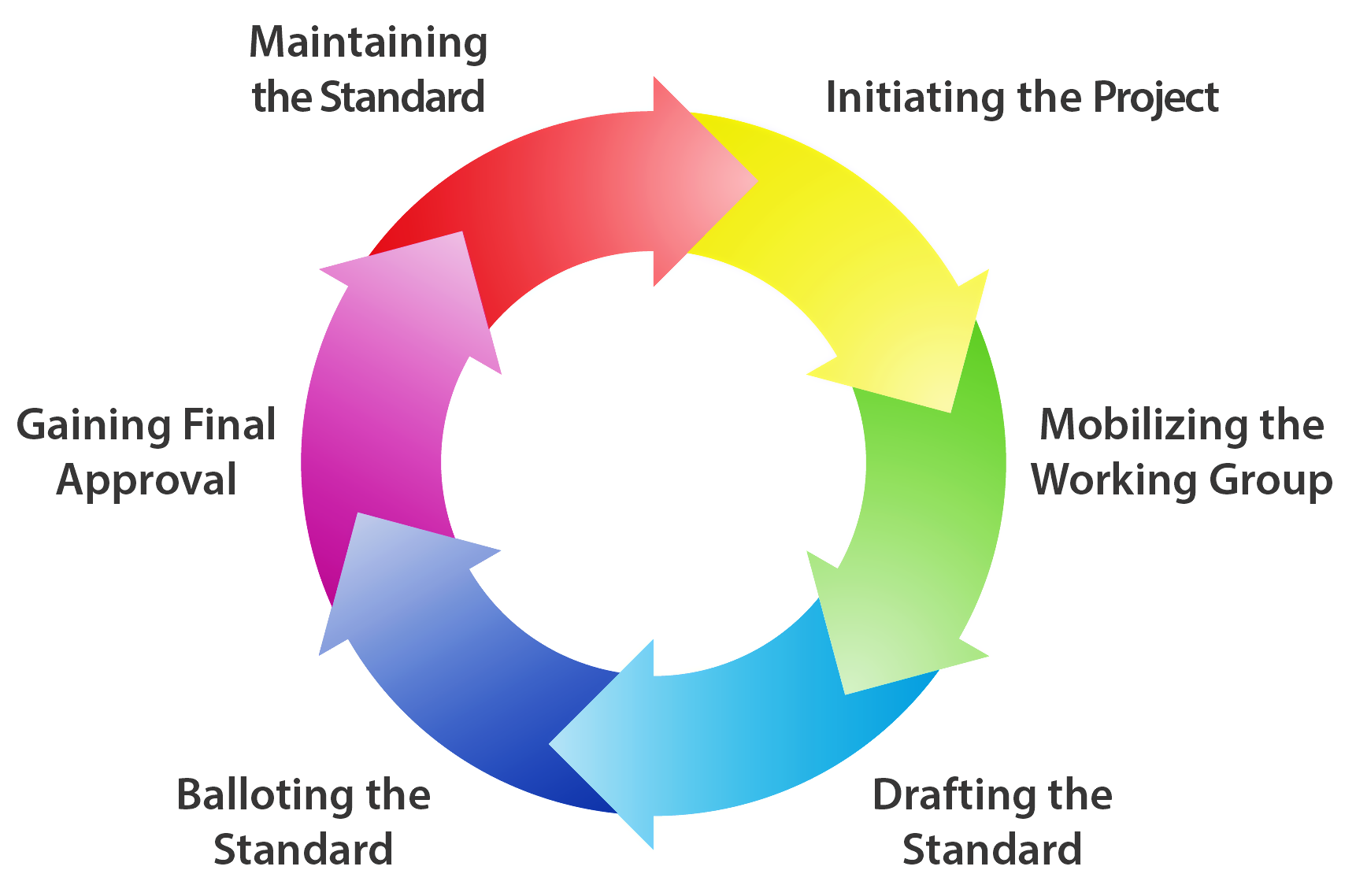
- Need for Customisation
- Adoption to project of different size
- Integration with standards demanded by different procurers – Integration with standards used by different developers
- Good Standards leave space for tailoring
- Good Standards provide guidelines about
- mandatory and optional practices
- the customisation process itself
- UK Govt Code of Technology Practice
- (🔗 https://www.gov.uk/government/publications/technology-code-of-practice/technology-code-of-practice)
- Define user needs, aims and capabilities
- Make things interoperable
- Make things open
- Make things secure
- Adopt cloud first
- Make things accessible
- Share and reuse
- Use common government solutions
- Meet the 🔗 Digital Service Standard for digital services
- Comply with the 🔗 Greening Government ICT strategy
- Define your sourcing strategy
- Demonstrate an end-to-end service
- Use common government sourcing routes
- Enter into sensible contracts
Tailoring Standards
Client Standards
Example